The North Korean Connection
Executive Summary
This report focuses on the complex laundering of thousands of BTC on behalf of the Lazarus Group, the infamous North Korean cyber crime group, by alleged conspirators engaged in money laundering on behalf of the group.
Bitcoin exchanges have been subject to mysterious hacks and breaches throughout bitcoin's history. Hacks and breaches are an inherent risk to custodial services that take control of user's private keys. The hacks are often attributed to exchange insiders, rogue, or even organized hackers.

Civil Action No. 20-606 was filed by the United States through the United States Attorney for the District of Colombia against "113 virtual currency accounts". The Complaint seeks to charge two Chinese nationals with aiding the laundering of thousands of stolen BTC on behalf of the Lazarus Group. This report will cover the following information based on the blockchain data provided in Civil Action No. 20-606:
- An overview of the hacks and available information provided in The Complaint
- Commentary on the alleged laundering of funds referenced in The Complaint
- An analysis of the on-going coin laundering alluded to in The Complaint
- Description of postmix spending behavior and destinations of mixed coins
The Complaint
On 2 March 2020, The United States Attorney for the District of Columbia filed Civil Action No. 20-606 based on investigations by the Internal Revenue Service — Criminal Investigations Cyber Crime Unit, Homeland Security, and Federal Bureau of Investigation.
The Complaint seeks asset forfeiture from "113 virtual currency accounts" allegedly controlled by two Chinese Nationals, Tian Yinyin and Li Jiadong (The Conspirators).
The Conspirators are charged with money laundering (18 U.S. Code § 1956) and operation of an unlicensed money service business (18 U.S. Code § 1960).
The Complaint includes partial documentation of the laundering of stolen funds acquired by hacking several South Korean Bitcoin exchanges.

The hackers gained access to exchange hot wallets through social-engineering and email phishing attacks. The Complaint links The Conspirators to North Korean operations based on evidence typical for cyber crimes. We cannot attest to the validity of these claims and expect that additional information has been withheld by law enforcement and security agencies as matters of national security.
While The Complaint does not mention the Lazarus Group, an update to the Office of Foreign Assets Control (OFAC) Specially Designated Nationals (SDN) list alleges The Conspirators are "linked to Lazarus Group."
Targeted Exchanges
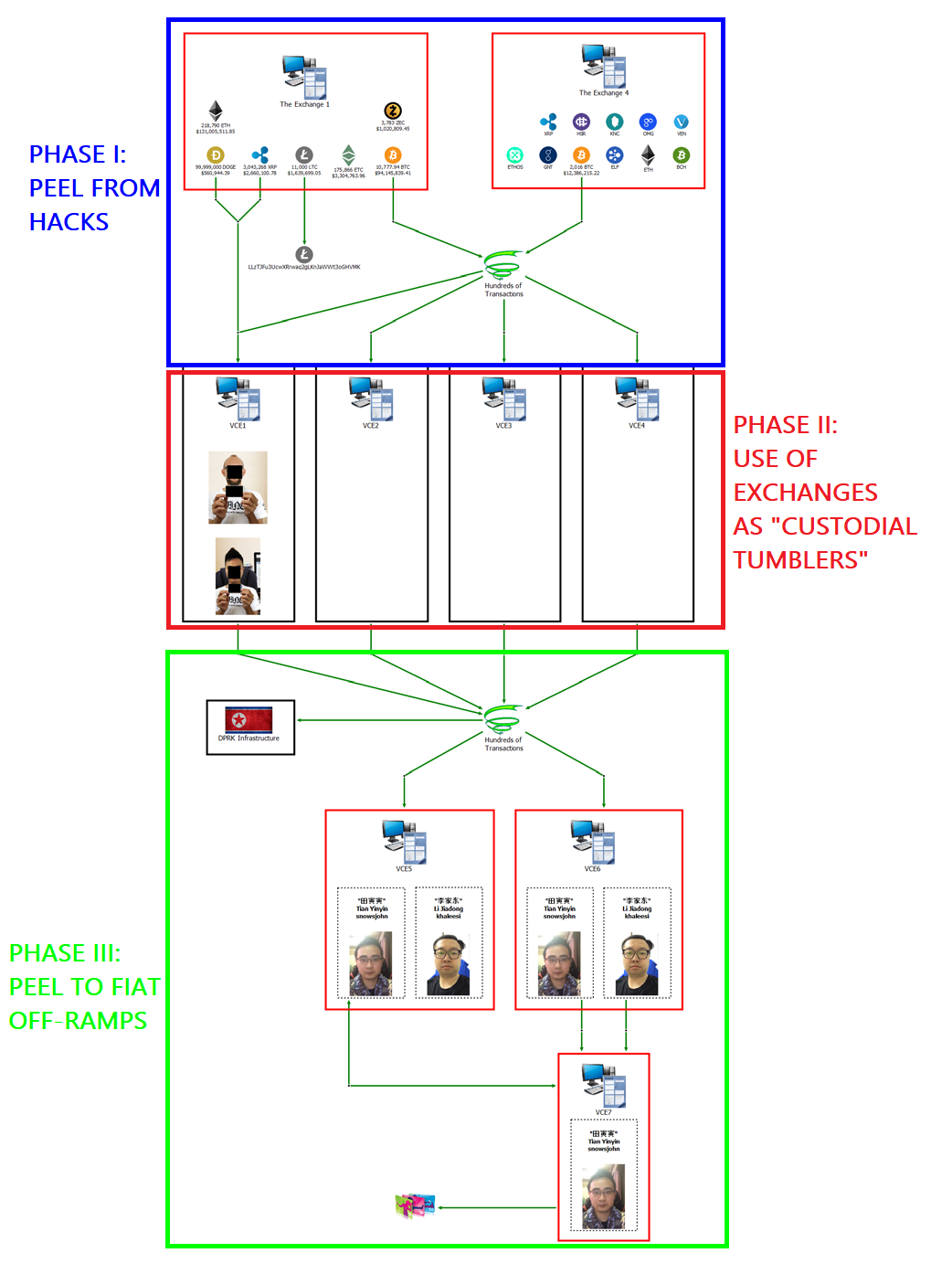
The Complaint breaks down the laundering of BTC and ETH from four exchange hacks in three phases.
The Complaint uses pseudonyms to refer to the exchanges involved in The Complaint and does not mention the exchange's actual names.
Details surrounding the hacks are generally limited to publicly available information from news reports including timing and volume of cryptocurrency hacked.
We have prepared a summary of the hacked exchanges based on publicly available information and addresses provided in The Complaint.
| Phase | Exchange | Amount Stolen | Breach Timeframe |
|---|---|---|---|
| I | Bithumb (The Exchange 1) | 10,777 BTC + crypto | Mid 2018 |
| I | Coinrail (The Exchange 4) | $40 million in crypto | Mid 2018 |
| II | Youbit (The Exchange 2) | 17% Assets | December 2018 |
| III | Upbit (The Exchange 3) | 342,000 ETH | November 2019 |
Defendant Properties and Entities
The Complaint lists 113 items including exchange IDs, bitcoin addresses, and other alt-coin addresses to be forfeited as a part of the Civil Action.
We have documented some of the relevant histories of these accounts including Complaint annotations, volumes sent/received, current balance, and activity dates. This data can be found on Item 1 in the attached spreadsheet.
On 6 March another 33 addresses were added to the forfeiture list. The majority of these are Ethereum addresses with a cumulative balance of over 91,000 ETH.
A list of the exchanges involved, and fund destinations sourced from public data and The Complaint Defendant Properties List are provided in Table 2, below.
| Complaint Pseudonym | Label | Defendant Properties |
|---|---|---|
| VCE 1 | HitBTC/Changelly | 63-64 |
| VCE 2 | KuCoin | 112 |
| VCE 3 | Bittrex (Etherscan) | 50-52 |
| VCE 4 | Yobit (ANON-1297295743) | 98-111 |
| VCE 5 | Huobi | 65-70 |
| VCE 6 | ANON-1168556017 (Unlabeled Exchange) | 55-62 |
| VCE 7 | Paxful (ANON-1420439095) | 83-84 |
| VCE 8 | Possibly DarkMarket (ANON-534406706), Related to ANON-1855602832 | 71-80 |
| VCE 9 | UpBit (Etherscan) | 113 |
| VCE 10 | Binance (Etherscan) | 44-49 |
| VCE 11 | Unlabeled (Etherscan) | 85-90 |
| VCE 12 | Unknown | 53-54 |
Updates to OFAC's SDN list
On 2 March 2020, the day of The Complaint filling, the OFAC SDN list was updated to include 20 bitcoin addresses also listed in The Complaint. The addresses are clustered among Huobi exchange and VCE 8, a possible Dark Net Market linked to ANON-1855602832.
The Office of Foreign Assets Control is a financial intelligence and enforcement agency of the U.S. Treasury Department. OFAC publishes a list of individuals and companies that U.S. persons are generally prohibited from dealing with.
Shortly after updating the OFAC sanctions list, 13 of the sanctioned addresses received small amounts of BTC, often referred to as "dusting", in a series of two transactions.
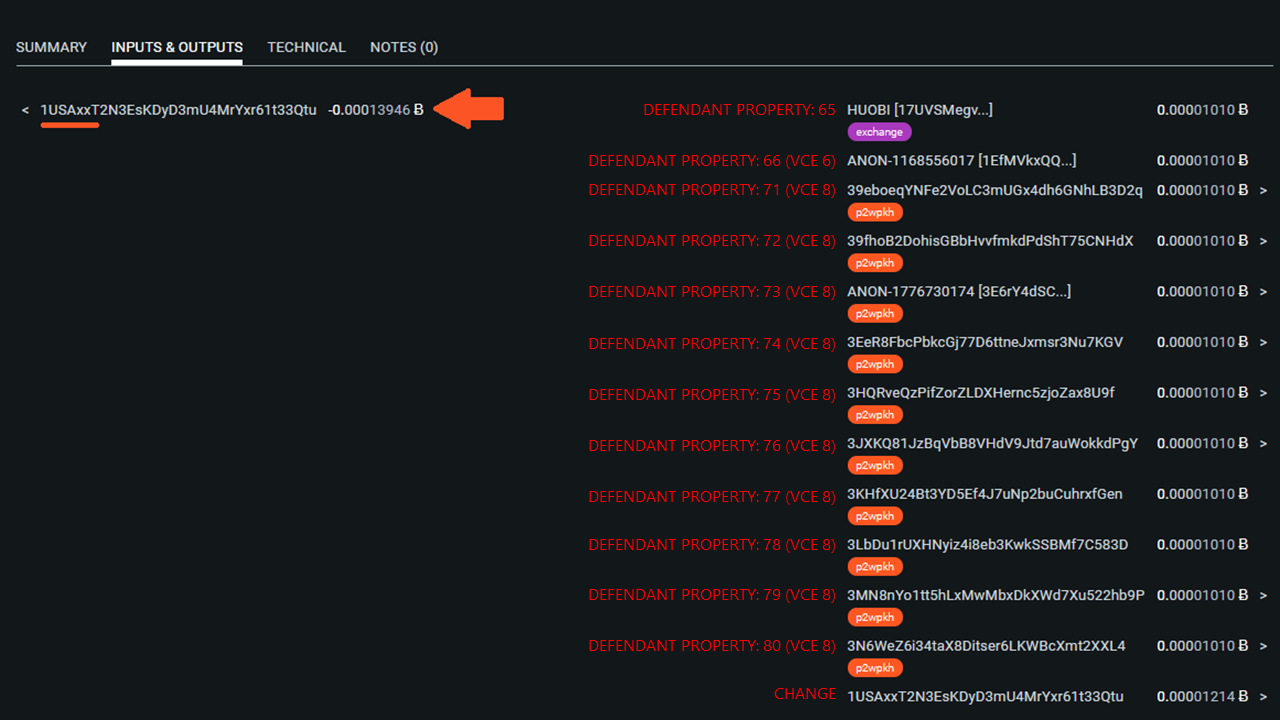
It's illegal to send fund to entities on OFAC's SDN list, though the possible vanity address may give some hints as to who may be responsible for the "dusting". It's worth noting that "dusting" of addresses on the OFAC sanctions list is common.
A list of the updated OFAC sanctioned addresses is provided in Item 2 of the spreadsheet attached below
The Laundering Process
The laundering of stolen coins described in The Complaint takes place in three distinct phases.
Phase I
Directly peel stolen funds from hacked or breached exchanges.
Phase II
Use of cryptocurrency exchanges that do not deal with government issued currency and therefore have less strict Know Your Customer (KYC) policies. These exchanges were used as a means of obscuring the origin of the stolen funds.
Phase III
Further peeling from the KYC-lite exchanges to exchanges with established off ramps into national currencies.
Phase I - Peeling Chains
Peeling chains have been implicated in the obfuscation of bitcoin transactions for some time. A peeling chain consists of a series of transactions with one input and two outputs. One of the transaction outputs (typically the smaller of the two) is interpreted as a payment to a third party. The second transaction output (typically the larger of the two) is interpreted as change back to the transaction sender.
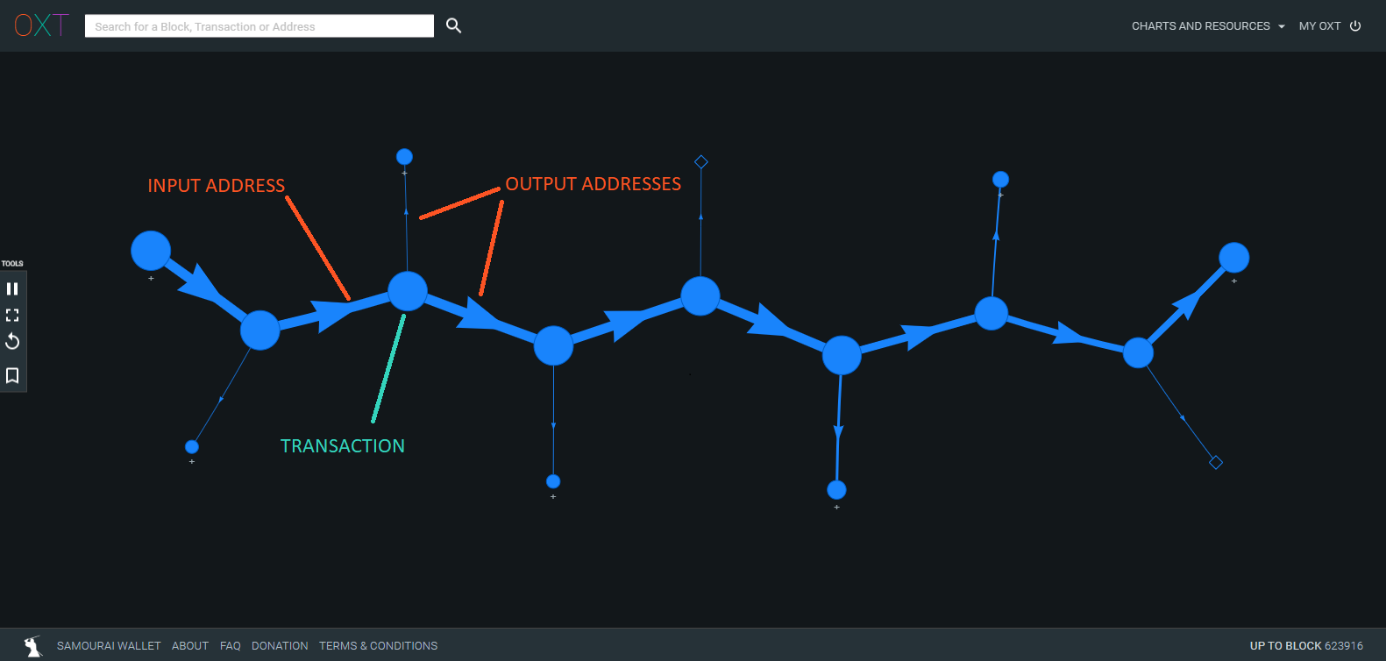
Most bitcoin transactions have one input and two outputs and produce peeling chain type transaction graphs. Where the implication of "laundering" enters the transaction graph interpretation is when a peeling chain is used to make multiple payments to the same entity.
Again, these transactions are generally traceable using a transaction graph tool, but peeling chains have the advantage of bypassing compliance software flags. Rather than making a single large value deposit to a service, the total deposit is made in smaller amounts over a series of transactions.
Phase II - Exchanges as Custodial Tumblers
While "peeling chains" are implicated as the predominant method of attempted laundering in The Complaint, the major obfuscation method used by The Conspirators was transfer through KYC-lite or KYC free exchanges as a part of Phase II.
The intent being to use the exchanges as custodial "tumblers". The act of simply operating a shared wallet makes tacking of inflows and outflows of exchange wallets difficult.
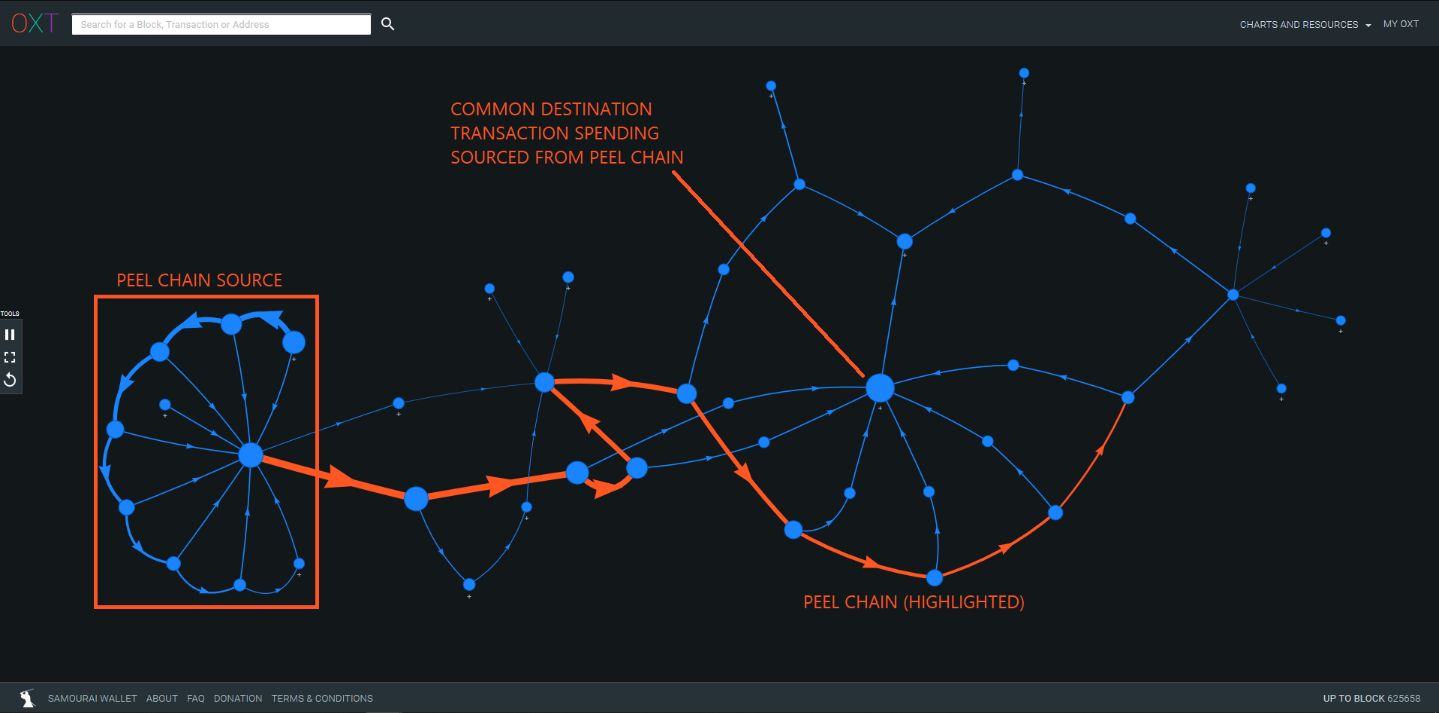
Phase III - Exit Via Fiat Exchanges with Fiat Off-Ramps
After attempting to break the links between the breached exchanges and the stolen funds using exchanges as custodial tumblers, The Conspirators peeled funds from the first round of exchanges to exchanges with established off-ramps into national currencies.
Exchanges with established off-ramps into national currencies often require KYC (Know Your Customer) information as part of their Anti Money Laundering (AML) polices including government ID that corresponds to a linked bank account and proof of address.
The Conspirators primarily cashed out into national currencies using the services at Huobi exchange and ANON-1168556017 (unlabeled exchange).
The Complaint alleges a total of 67.3 million USD in withdrawals from the noted exchanges to multiple Chinese banks. In addition, The Conspirators cashed out nearly 1.5 million dollars in iTunes giftcards using the Paxful peer-to-peer exchange.
Mixing of Laundered Funds
The majority of The Complaint addresses in the Defendants Properties list are associated directly with exchanges with the exception of the first 34 addresses which are traceable to the conversion of ETH from the November 2019 Upbit hack. The Complaint details the circumstances around these addresses:
...approximately 18 different clusters, comprised of approximately 200 different BTC addresses (including Defendant Properties 1 through 34 and Defendant Property 91), that received 383.79970162 BTC ($2,781,754.23) from November 29, 2019 through January 4, 2020. Each of these clusters received BTC that was converted from ETH proceeds traced to the theft of The Exchange 3... From these 18 clusters, the subjects began to layer with peel chains and mix [emphasis added] the BTC, in order to obfuscate the trail as they converted it to fiat currency. The peel chains from these clusters were connected to each other.
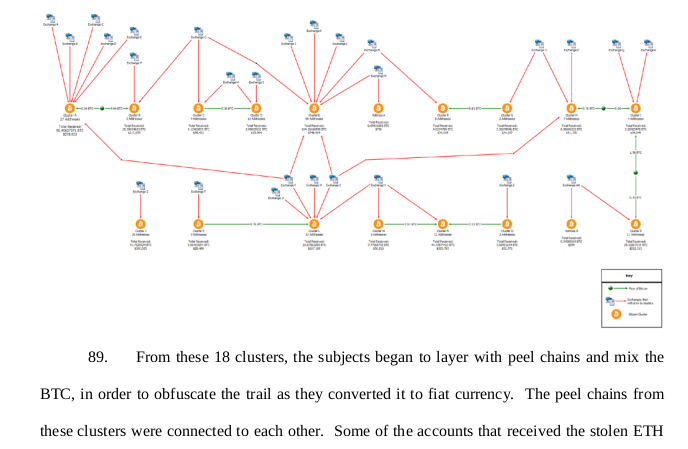
Linking the Properties
Defendant properties 1 through 34 are clustered into ANON-2569993443.
Of the 11 outbound transactions from this cluster, most are combined with funds from the 18 clusters described above. Three outbound transactions from ANON-2569993443 are peeled to exchanges in a process similar to that described in The Complaint.
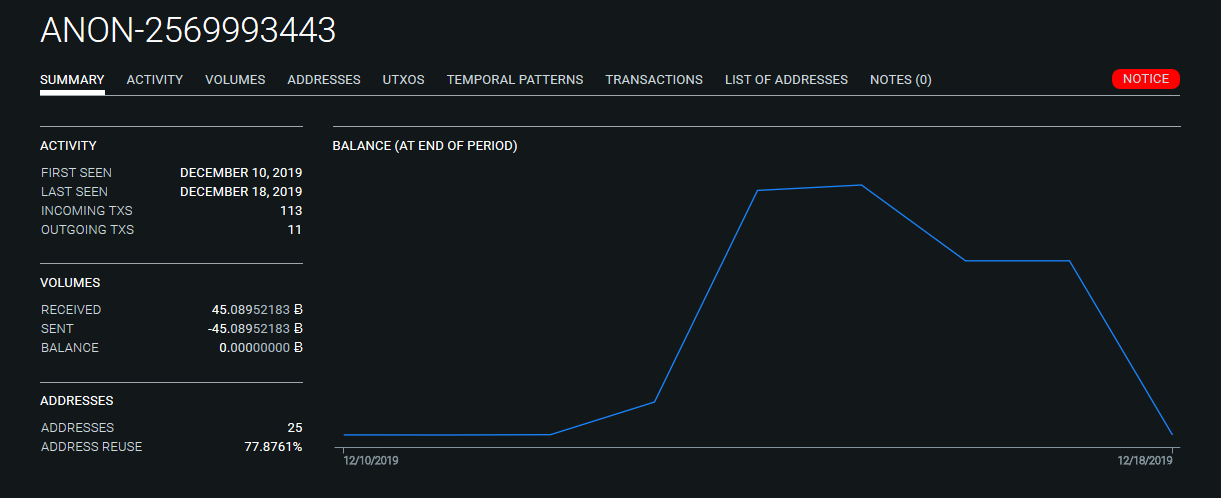
The remaining 8 transactions are sent to two separate mixers, the custodial tumbler ChipMixer and non-custodial Wasabi CoinJoin implementation. Additional details of ANON-2569993443 are provided in Item 3 on the attached spreadsheet.
While "mixing" is only implicated once in The Complaint, we have found significant links to several mixers totaling in the thousands of BTC since mid-December 2019 alone.
Unwinding The Mixing Process
The graph below traces the flow of funds out of cluster ANON-2569993443 via TxID (f73d1...). The outgoing funds are split into two branches.
Branch A => ChipMixer
aggregates funds from the 18 clusters referenced in The Complaint before sending to ChipMixer, a custodial tumbler.
Branch B => Wasabi
aggregates funds from The Conspirators clusters followed by a second round of aggregation with funds from ANON-1855602832 before depositing into the Wasabi mixer.
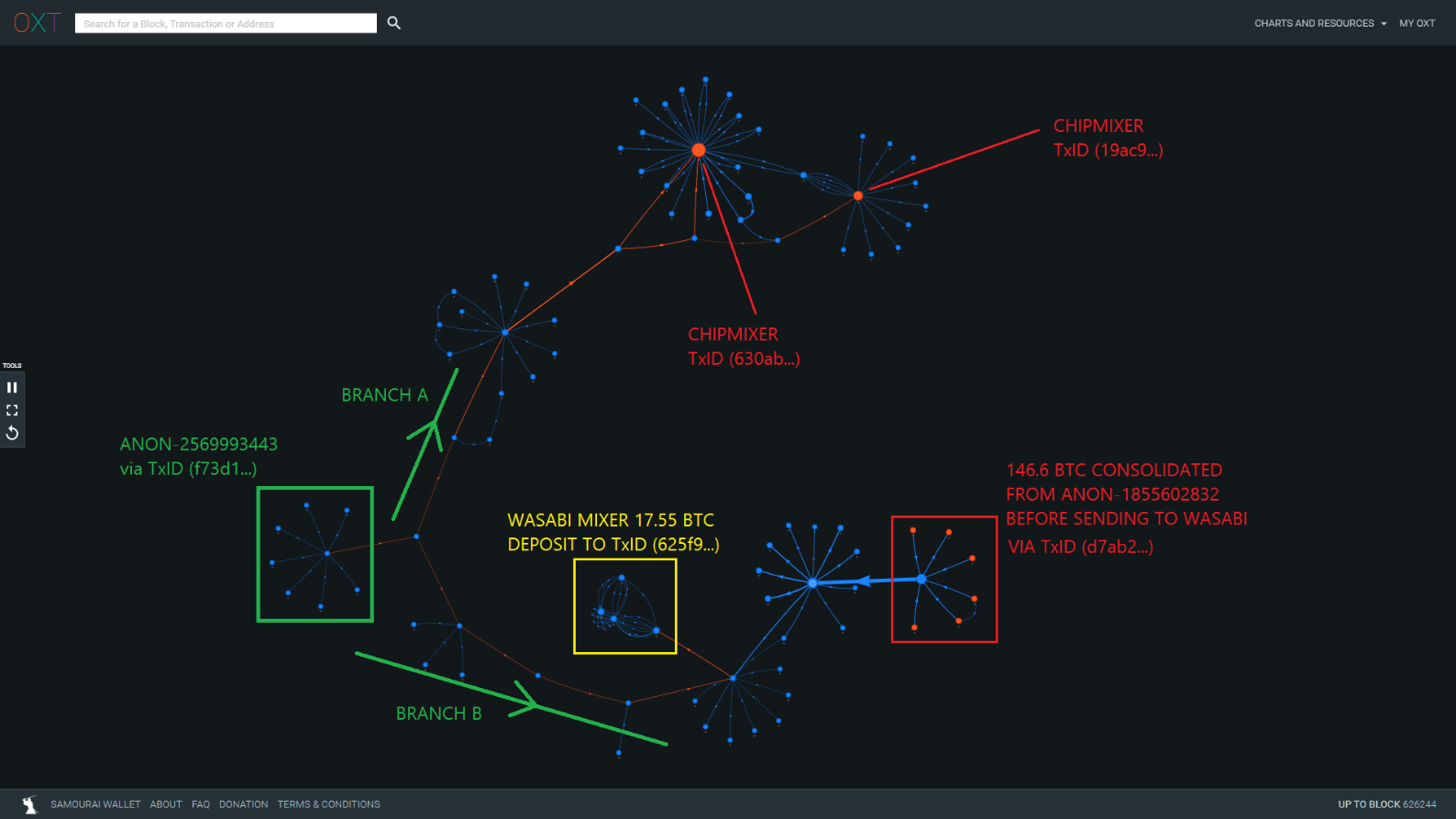
The consolidation of funds from The Conspirator's cluster and ANON-1855602832 indicates that The Conspirators may be responsible for the significant Wasabi mixer volume from ANON-1855602832 since mid-December.
Introducing ChipMixer
ChipMixer is a custodial tumbler that operates differently from Chaumian style CoinJoins in that the tumbler takes custody of the user's private keys, and can at any time steal the funds.
This can present a challenge to tracking the flow of funds across the mixer because funds returned to the user may not be returned as outputs from the same transaction as the mixer deposit. In effect this severs the transaction graph and can make tracking of funds across the tumblers more difficult.
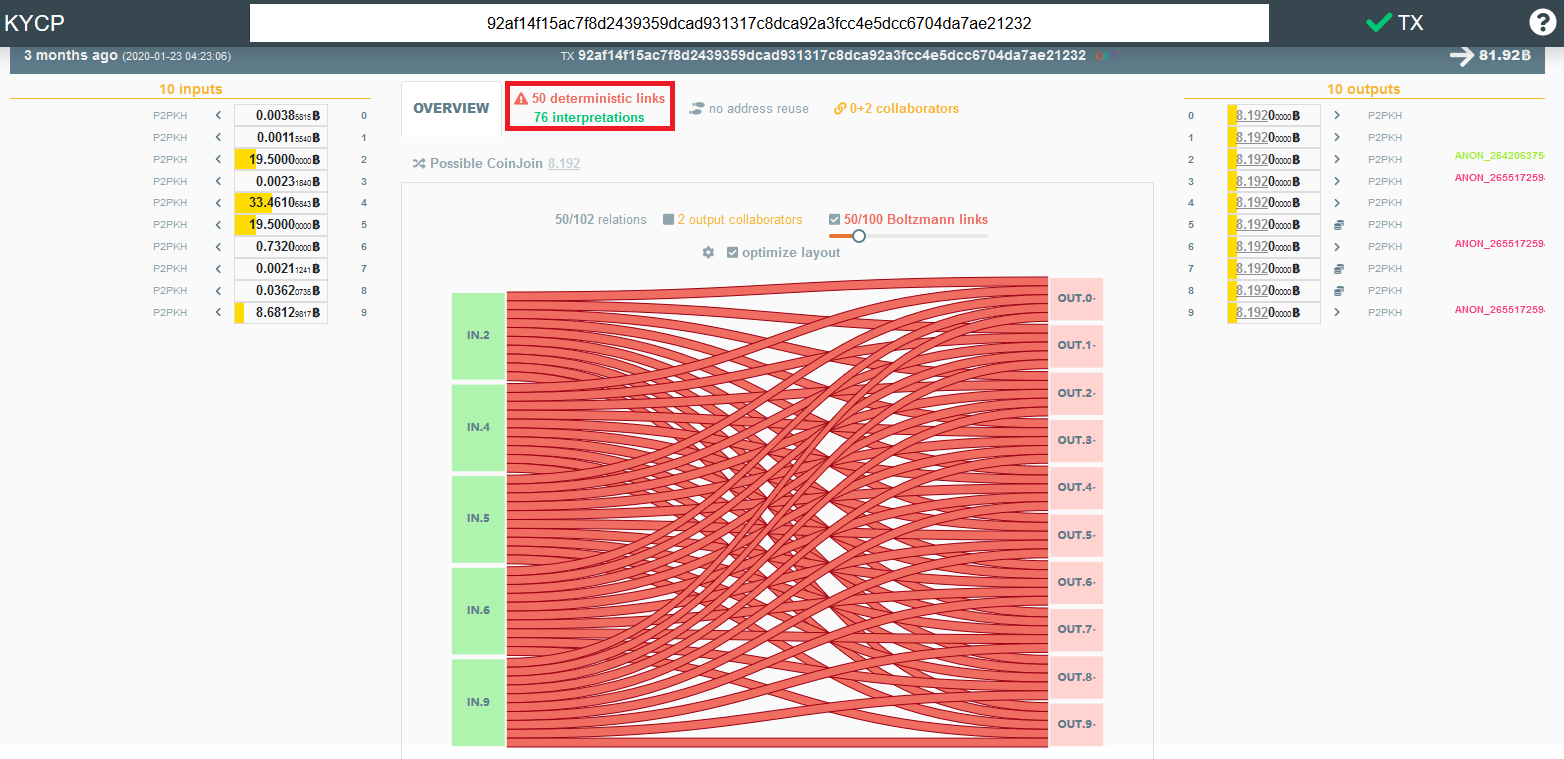
ChipMixer transactions are easily identifiable because they produce mixed outputs that are exact multiples of 0.001 BTC. Additional ChipMixer outputs include 0.002 BTC, 0.004 BTC, 0.008 BTC, and so on up to a maximum of 8.192 BTC (that we have seen). An example of a weak ChipMixer transaction is provided below. The large inputs fail the CoinJoin Sudoku test resulting in deterministic links.
Unwinding ChipMixer
Despite the custodial architecture - which traditionally would offer more privacy at the cost of risk of total loss - tracking of funds across ChipMixer is simple when large volumes originating from the same source are returned in the same transaction.
Additional metadata can be used to verify that funds are returned to the user in the same transaction. We leveraged the following metadata to de-anonymize The Conspirator's transfers across ChipMixer:
- Volume correlation between inputs and outputs
- Common sources of inputs and destinations of outputs
- The combination of premix coins and postmix coins
Eight outbound transactions out of cluster ANON-2569993443 were included in three ChipMixer transactions (630a4..., c3ad..., 19ac9...).
As a part of the tumbling process, The Conspirators aggregated funds from the 18 clusters and made multiple simultaneous deposits of approximately 20 BTC into the tumbler.
Tumbler TxID (19ac9...) was particularly damaging to the attempted laundering when The Conspirators deposited nearly 160 BTC into the same transaction. The tumbled coins were consolidated and peeled in varying directions. Several peel branches were later consolidated in a 100 BTC deposit to Huobi address [15qRSE...].
This address has received significant volumes from ChipMixer transactions that were likely sourced from additional clusters controlled by The Conspirators.
The following transaction graph depicts the metadata used to de-anonymize the flow of Conspirator funds across ChipMixer and into Huobi.
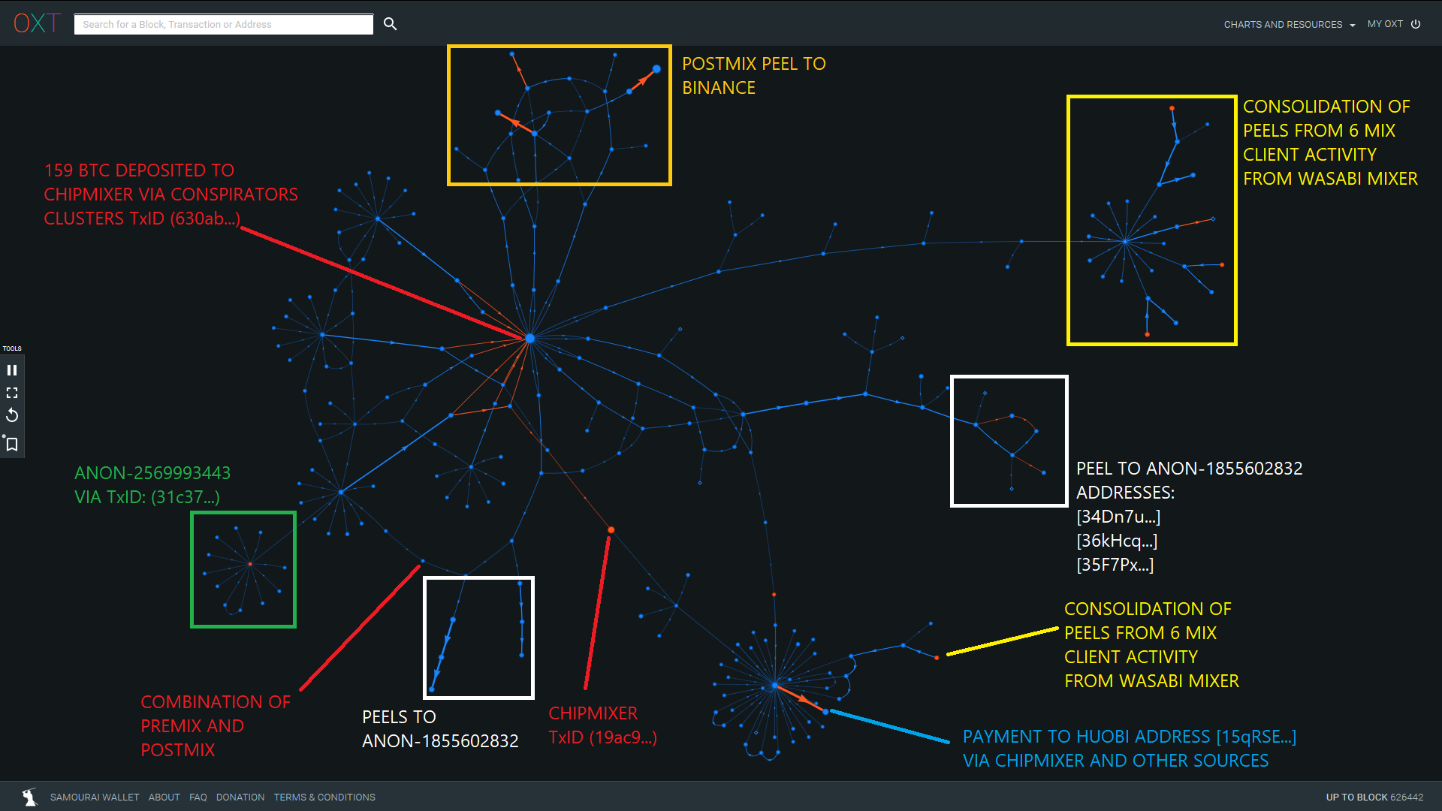
The postmix behavior shows multiple peeling chains to various destinations including:
- Binance
- The postmix spending to ANON-1855602832 is the second noteworthy relationship between The Conspirators and the cluster. Funds were sent to the following addresses:
- [34Dn7U...] — 3372.7 BTC received in total
- [35F7Px...] — 2668 BTC received in total
- [36kHcq...] — 1725.6 BTC received in total
- Huobi Address [15qRSE...] — 1316.5 BTC received in total during January 2020. This address has received several transactions from various sources, but a noteworthy portion of the volume received is sourced from ChipMixer.
A sampling of postmix peel origins and noteworthy exchange destinations is included in Item 4 of the attached spreadsheet.
Introducing Wasabi
Our first indication that The Conspirators have been laundering funds through Wasabi CoinJoins can be found in Branch B of Figure 11 above.
The funds from the Conspirator's cluster were aggregated with coins from ANON-1855602832 , an entity with ties to VCE 8 (ANON-534406706), prior to depositing into Wasabi.
The Conspirator's may be attempting to use ANON-1855602832 as a custodial "tumbler" before sending through Wasabi CoinJoins.
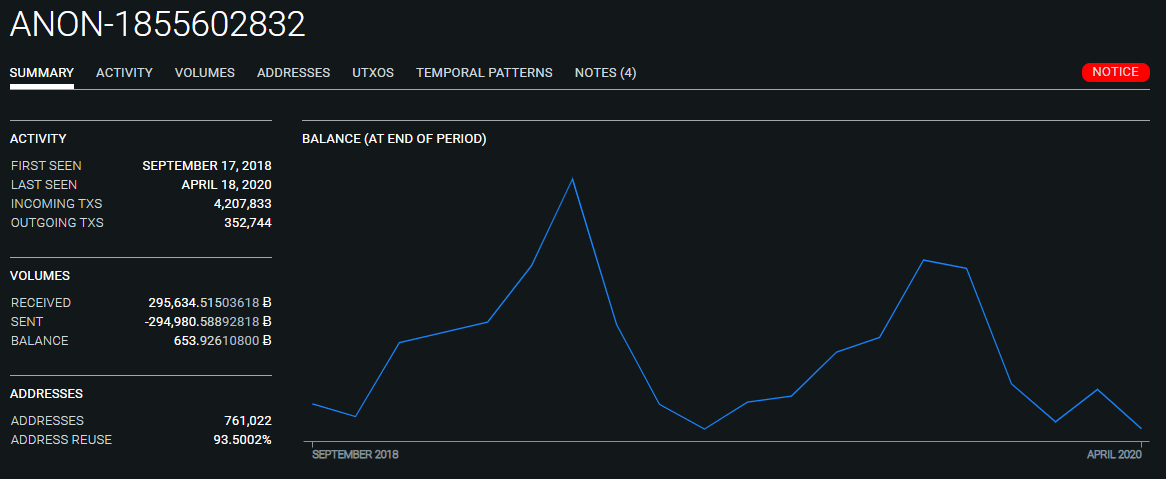
Unwinding Wasabi
The deposit to Huobi address [15qRSE...] via TxID (895fb...) received roughly 11.85 BTC distributed from a peeling chain via postmix TxID (c842c...), sourced from Wasabi CoinJoins.
This postmix transaction was unique, in that it consolidated up to 6 identical sized mixer outputs from the same mix transaction. Indicating that The Conspirators are operating up to 6 simultaneous Wasabi mixing clients in behavior consistent with a Sybil Attack.
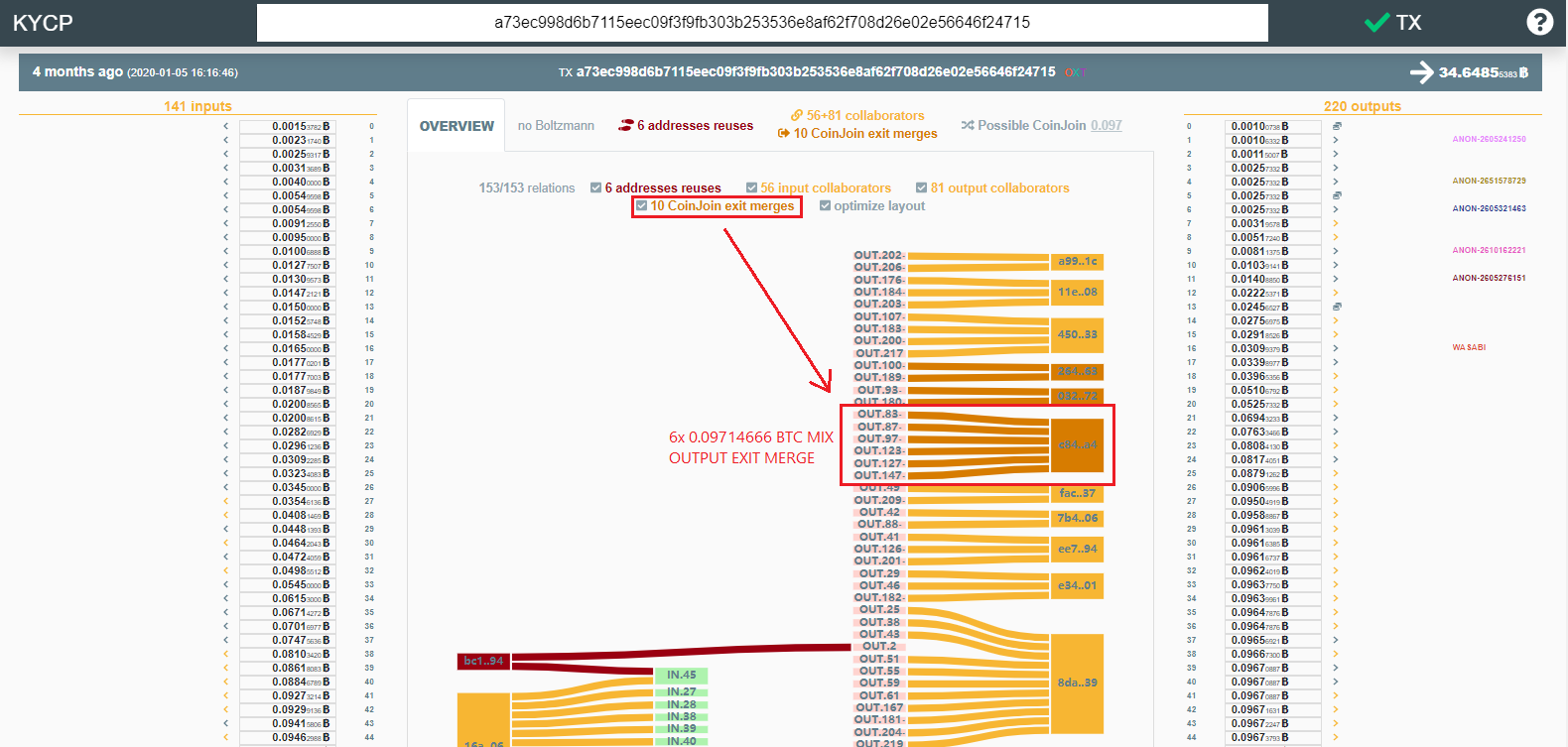
Following the large unmixed change back across the mixer leads back to TxID (eb0fd...) which was responsible for depositing 300 BTC into the Wasabi mixer on 31 December 2019.
This transaction made up to 6 deposits into the same mix above the minimum mix amount. As a result, this mixer deposit is an obvious source for the outgoing transaction that was sent to The Conspirator's Huobi address.
Expanding the transaction history from the 6 mixing client source showed an additional 100 BTC using 5 mixing clients from late December and two 2 separate 100 BTC deposits in late January.
Based on the relationship with the post ChipMixer spending, this source is likely controlled by The Conspirators.
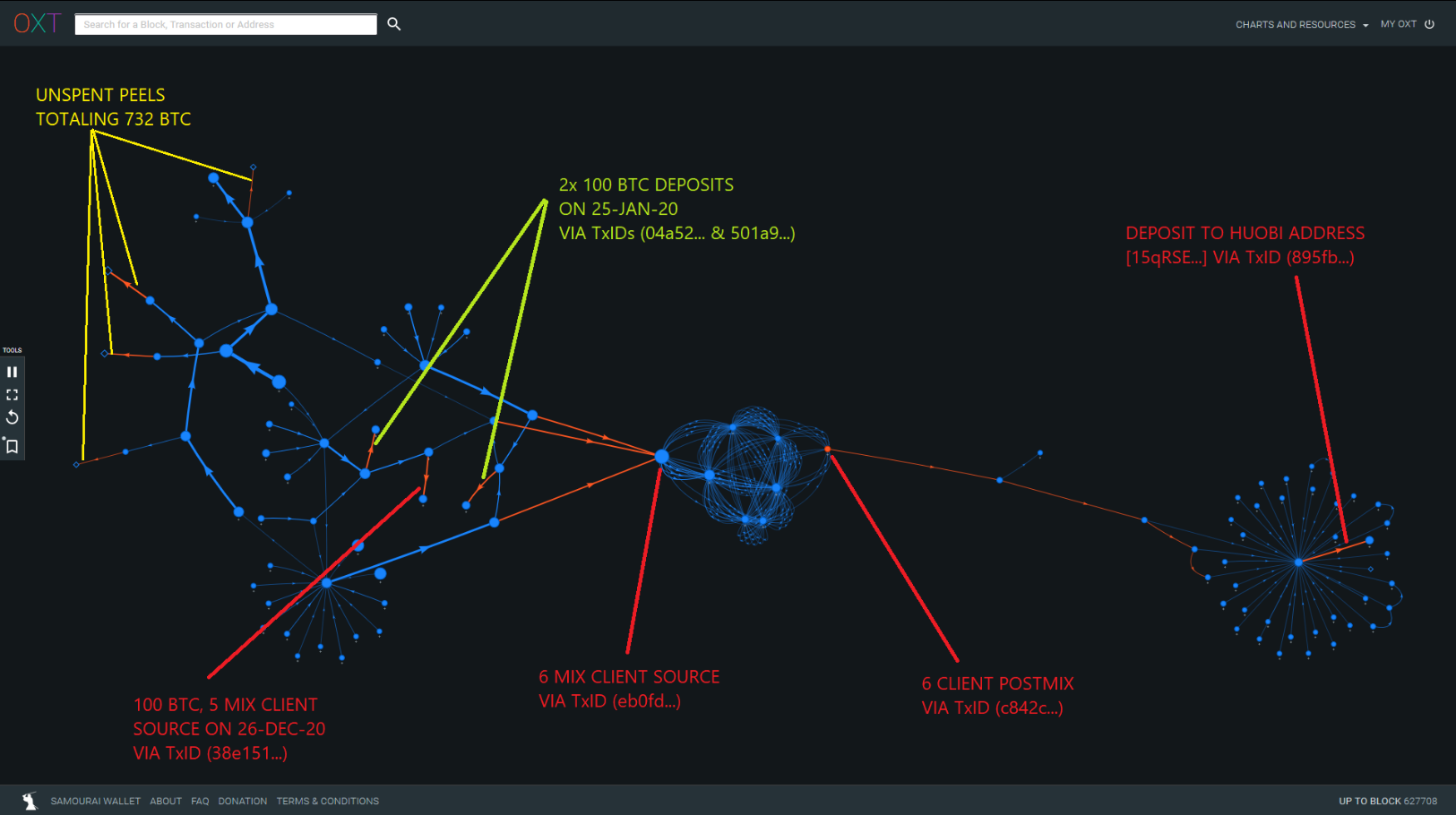
This premix cluster was mostly sourced from ANON-493679302 in March 2015 with close ties to the custodial tumbler Bitcoin Fog.
Peeling chains originating from this premix cluster are also attributable to 732 unspent BTC that are possibly controlled by The Conspirators.
A list of addresses containing these unspent funds are included in the attached spreadsheet. A detailed list of transactions and addresses associated with this cluster are provided in Item 5 of the attached spreadsheet.
Cumulative Design Flaws and De-anonymization Across Wasabi
The Conspirator and ANON-1855602832 flows across Wasabi are easily trackable due to unequal amount CoinJoins, lack of structural liquidity enforcement, operating multiple mixing clients, and poor post-mix practices.
In addition to these poor practices, we have encountered a critical design flaw within the Wasabi mixer due to a cumulative set of failures. These separate sub-optimal practices may not be critical in isolation, but when aligned, result in automatic clustering and de-anonymization of fund transfer across Wasabi. The independent flaws are as follows:
- Peeling Style Coinjoin Implementation
The inclusion of "unmixed change" within CoinJoin transactions that are deterministically linked to mixer deposits. - Address Reuse
A common privacy worst practice that confirms common ownership of UTXOs and results in clustering within the mixer. - Lack of Postmix Spending Tools
Actively creates or maintains clusters upon exiting the mixer.
The flaws noted above create automatic clustering and de-anonymization when address reuse results in clustering of "unmixed change".
As described above, the unmixed change is deterministically linkable to the mixer deposits. If the cluster persists throughout the mixing process, and is not broken by postmix spending, the outbound spending cluster will still be clustered with the "unmixed" change resulting in de-anonymization of funds.
Exploiting the Flaws
These compounding flaws are illustrated by the following cluster. The failure process is as follows:
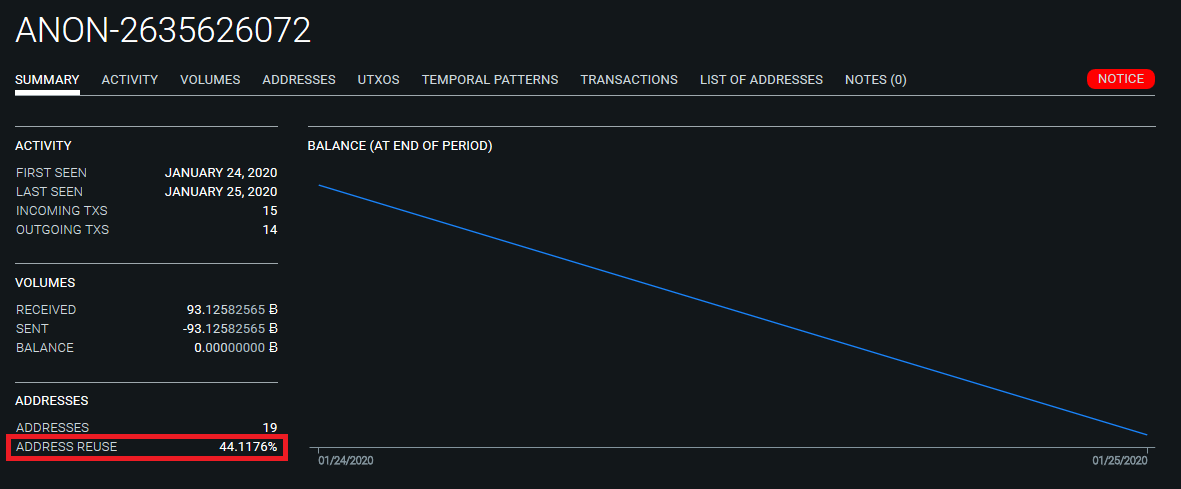
- 37 BTC Deposit by the ANON-1855602832 Whale via TxID (573f3...)
- Address Reuse clusters 34.8 BTC "unmixed change" output to ANON-2635626072 mix TxID (98a3d...)
- Cluster ANON-2635626072 grows during mixing process
- Cluster persists on postmix spending example via TxID (1f37ae...)
Anon-1855602832 Whale and Wasabi
The ANON-1855602832 Whale has been a noteworthy source of Wasabi volume throughout 2019. Most of these deposits are likely not attributable to The Conspirators. However, we have noted significant volume deposited into the mixer originating from ANON-1855602832 since mid-December that follows a similar pattern.
Funds are withdrawn from the cluster, then aggregated in large batches before sending to Wasabi CoinJoins in a staggered fashion. A list of notable Wasabi deposits transactions sourced from ANON-1855602832 are included in Item 6 of the attached spreadsheet.
Many of these deposits are linkable through undeposited change indicating these funds are controlled by the same entity.
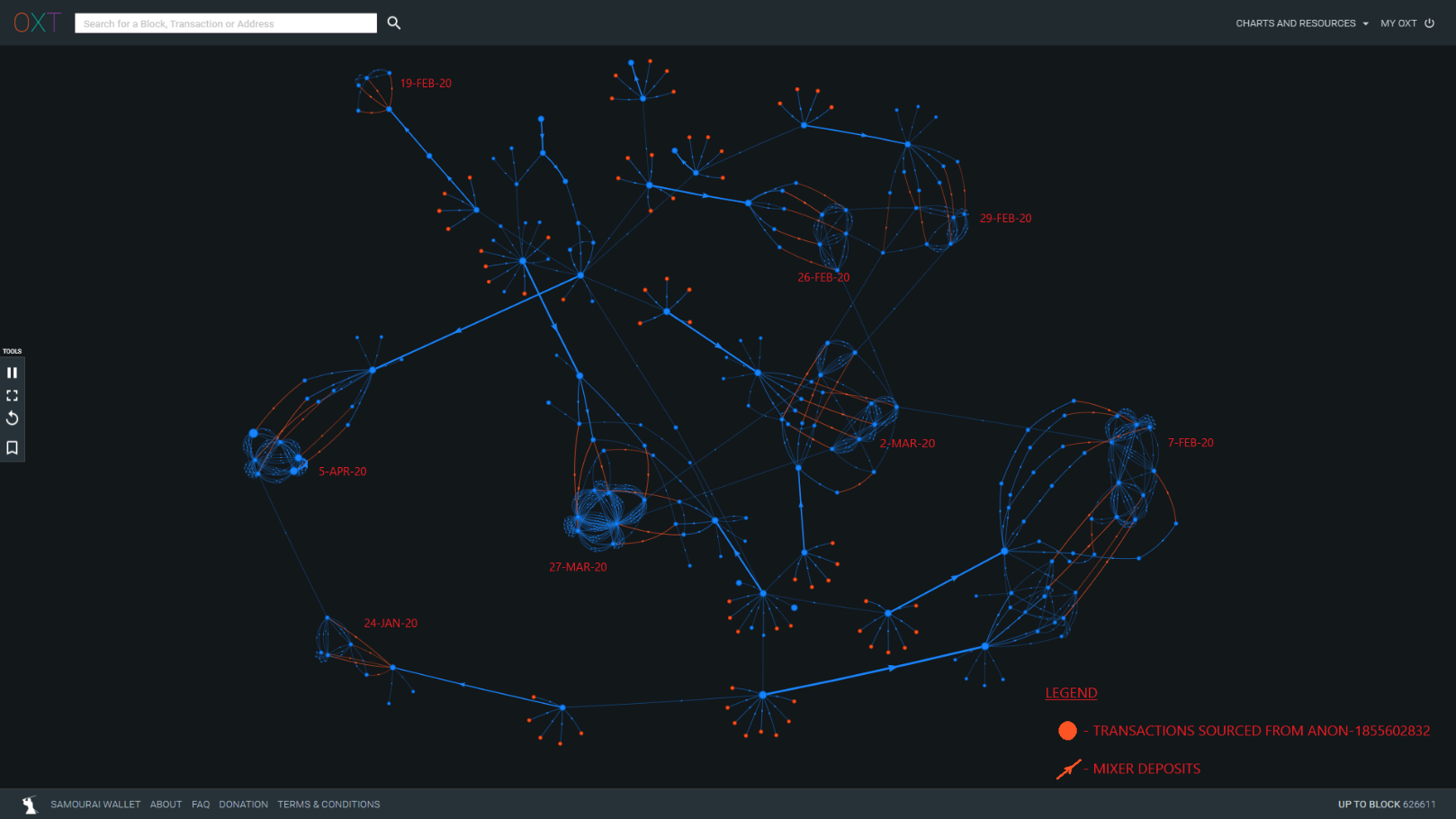
Approximately 4500 BTC sourced from ANON-1855602832 has entered Wasabi CoinJoins since mid-December. In addition, the ANON-1855602832 Whale appears to be operating at least two mixing clients based on the CoinJoin deposits sourced from TxID (a7aad...).
The Whale's mixing behavior typically follows the pattern described below and illustrated in Figure 17:
- A - Withdrawal and consolidate outputs from ANON-1855602832, followed by staggered deposits into CoinJoins. Coins are typically sent through a single CoinJoin round. Example TxIDs (d34d2..., 7fe7a...).
- B - The CoinJoined outputs are then withdrawn one or two at a time to an external wallet as evidenced by the change in address type (P2SH). The withdrawals are consolidated again in an additional transaction. Example TxIDs (b85e9..., a9694...).
- C - The consolidated outputs are then consolidated further and peeled to various exchanges. Example TxID (9d868...).
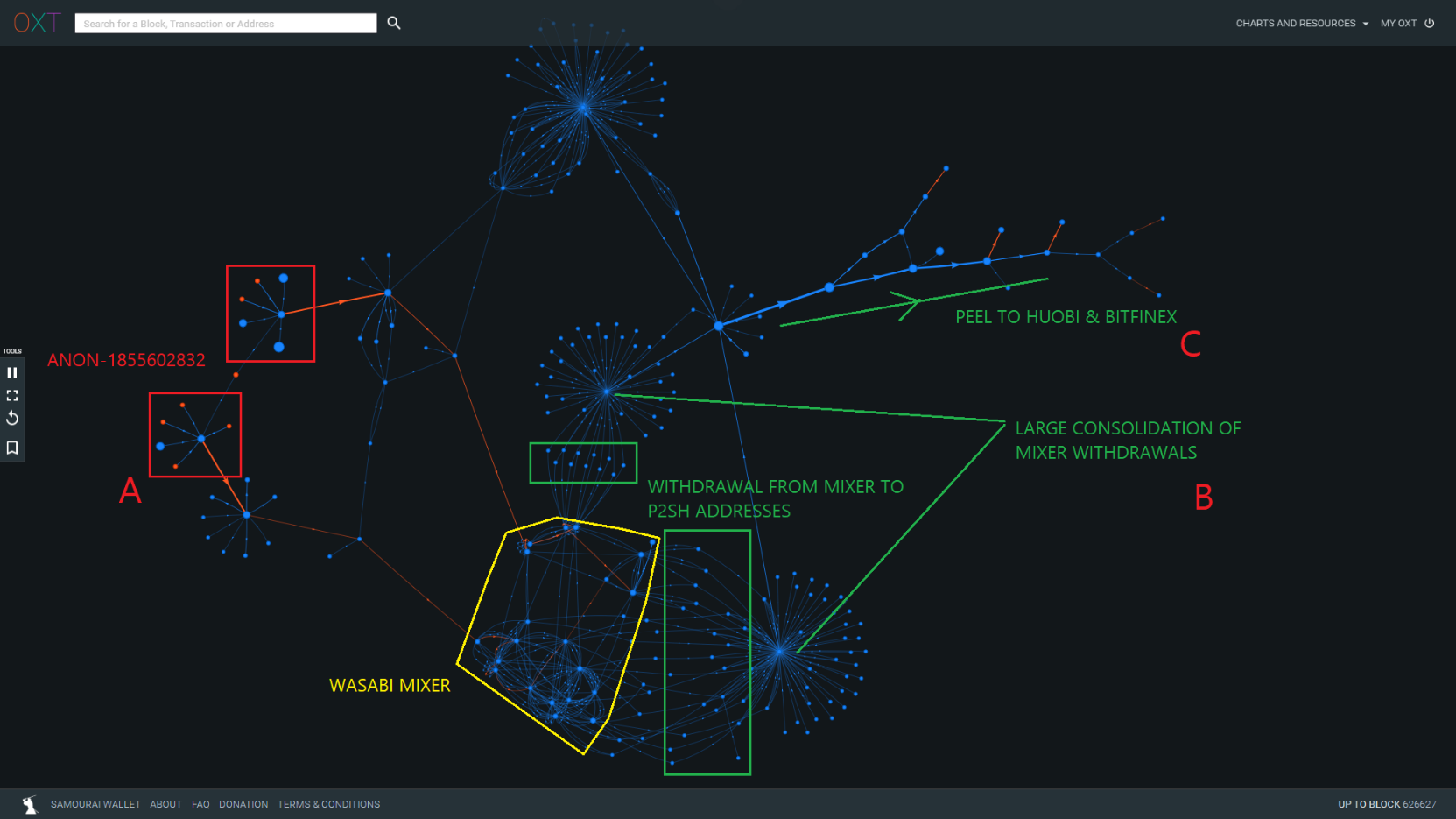
Occasionally, large "unmixed change" outputs sourced from ANON-1855602832 are partially peeled through several CoinJoin rounds before aborting mixing early. The "unmixed change" is then consolidated with mixed outputs before distribution to exchanges or being re-injected into the mixer.
Connecting the Conspirators and the Anon-1855602832 Whale
So far, we have noted the following links between The Conspirators and ANON-1855602832:
- The Conspirators were allegedly posting advertisements at VCE 8, a possible Dark Net Market. Several Conspirator addresses on the OFAC sanctions list are associated with VCE 8 (ANON-534406706), which has ties to ANON-1855602832.
- Funds from the Defendant Property list were merged with outputs from ANON-1855602832 prior to sending to Wasabi CoinJoins.
- Funds flowed from Items on the Defendant Property List, through ChipMixer and into ANON-1855602832. Specifically, funds flowed into the following addresses:
- [34Dn7U...] — 3372.7 BTC received in total
- [35F7Px...] — 2668 BTC received in total
- [36kHcq...] — 1725.6 BTC received in total
The Conspirators may be using ANON-1855602832 as a custodial tumbler similar to the first round of exchanges noted in The Complaint.
We have also described two unique mixing behaviors associated with Wasabi:
- The 6 mixing client entity who is linkable to The Conspirators addresses through ChipMixer.
- The ANON-1855602832 whale which has the weaker relationships noted above.
Both behaviors were noted during a brief period between 24 and 25 January. Deposits associated with both behaviors were made via the following TxIDs (045a5..., 6 Client Entity) and TxID (573f3..., ANON-1855602832). During this time, we did not note any consolidation of separate postmix funds attributable to the entities.
Postmix Destinations
After mixing, The Conspirators typically consolidate their mixed coins before engaging in peeling chains to multiple exchanges. The peeling process is quite complex, but we have noticed several recurring exchange address destinations in the ChipMixer and Wasabi mixer behavior. A short list of preferred exchanges is provided below:
- Huobi: likely for cashing out
- OkEx: likely for cashing out
- Binance
- Bitflyer
- Bitfinex
- Fcoin (now shutdown): likely to be used as a secondary custodial mixer
- ANON-1855602832 as a pass-through entity
A sampling of recurring destinations and addresses are compiled in Item 4 of the attached spreadsheet.
Many of these addresses may be generic exchange hot wallets. However, several of the addresses appear more dedicated to receiving funds from The Conspirators.
Conclusions
In this report, we have covered the following:
- An overview of The Complaint including evaluation of the techniques used by The Conspirators and annotated list of hacked exchanges and destinations of the laundered funds.
- An evaluation and overview of where The Complaint analysis ends, with a particular focus on the use of ChipMixer and the Wasabi Mixer by The Conspirators.
- An evaluation of possible remaining unmixed funds controlled by the scammers (totaling 732 BTC) which are attributable to The Conspirators.
- A list of preferred destinations for mixed funds including compliant exchanges such as Huobi, OkEx, Bitfinex, BitFlyer, and Fcoin.
- A discussion of the links between The Conspirators, the ANON-1855602832 whale, and Wasabi mixing, which for now remains unclear.
- Despite the inherent risks to users in sending funds through custodial mixers, these style mixers provide architectural advantages that can make tracking of coins more difficult than coins mixed through non-custodial CoinJoin implementations with architectural flaws.
- Evaluation and tracking of funds across multiple mixers with the following take-aways:
- Analysis of abnormal volume and evaluation of entities operating multiple mixing clients allows for easier de-anonymization.
- The mixing behavior of the ANON-1855602832 whale has illustrated a series of cumulative design flaws with the Wasabi mixer resulting in deterministic de-anonymization.
The process described in The Complaint involves hundreds of transactions and intermediaries including mixers, making the tracking of funds very difficult. The use of exchanges as custodial mixers is particularly challenging and makes a purely transaction graph-based analysis nearly impossible. However, the transaction graph can be used to leverage metadata to track the flow of funds across mixers. It's very likely that we will be revisiting this situation in the future.
Our analysis leveraged the power of the OXT platform in combination with unique knowledge of bitcoin mixers and a flexible targeted evaluation to track the movement of these funds.
The OXT Research Team is intimately familiar with the analysis of special situations affecting bitcoin markets. With the help of the OXT platform, we remain uniquely situated to provide targeted transparent analysis of this and other special situations affecting bitcoin.
