The Liquid Global Hack
It’s being made available now for posterity and the introduction of a “new” tumbler that will be featured in future OXT-R forensic reports.
The forgotten hack.
Another year, another hack of a small Asia based crypto exchange.This time Liquid Global.
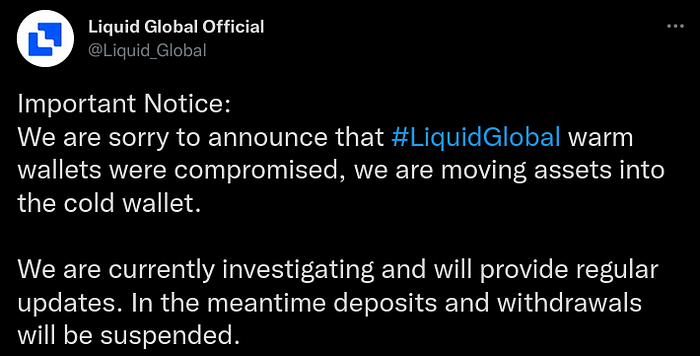
Hack Overview:
- Situation updates can be found on Liquid Global’s blog and the Liquid Global Twitter feed.
- Timestamp: Approximately 20:00 UTC 18 August 2021
- USD Value: Approximately $91 million
- Stolen Token Sample: BTC, ETH, TRX, XRP, stable coins, and other ETH tokens
Shortly after the hack, reports of altcoin movements to decentralized exchanges and attempted obfuscation of the stolen ETH were reported on social media.
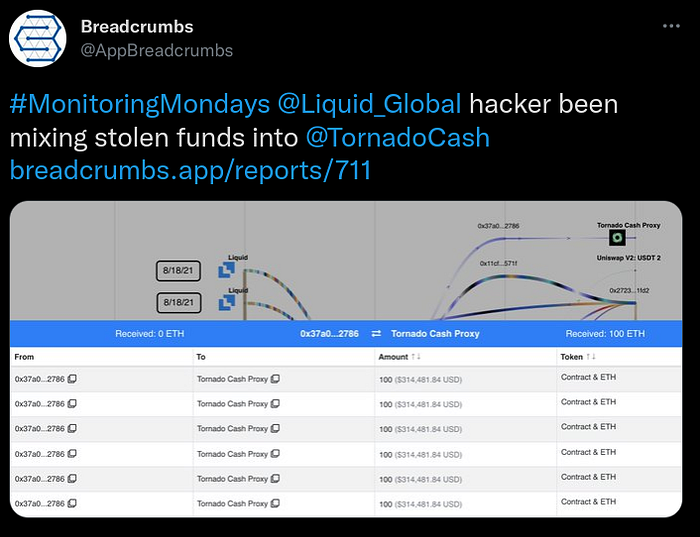
The crypto movements during the early stages of the Liquid Global hack had several similarities with the 2020 KuCoin hack. Readers are encouraged to review our report on the KuCoin hack before continuing this report.
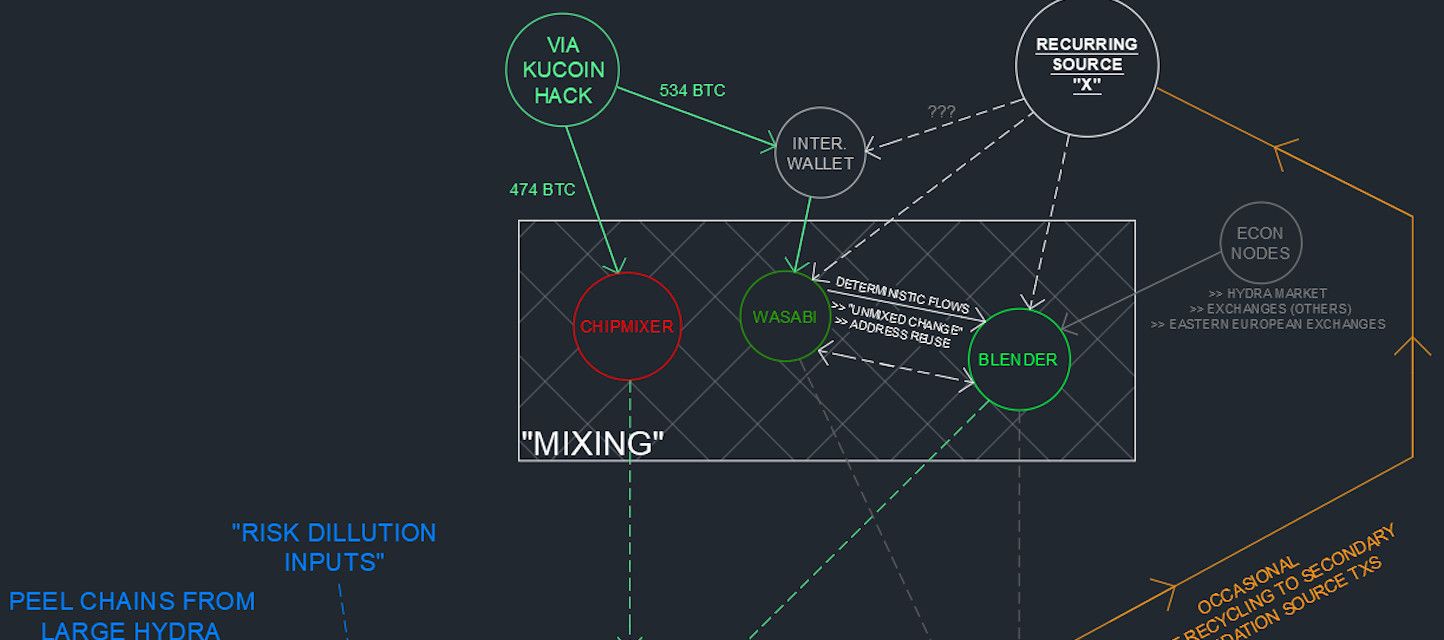
The similarities between the KuCoin hack and the Liquid Global hack include:
- Targeting of a small Asia based exchange
- Preference for movement of altcoins and tokens prior to moving the stolen BTC
- Similar BTC address formats, wallet fingerprints, and destinations of the associated BTC
ATTRIBUTION PROCESS SUMMARY
The following is an overview of our attribution methodology:
- Identify large Wasabi inflows
- Identification of Wasabi inflows with Blender transaction fingerprints
- Backtracking of Blender fingerprint flows to starting point on BTC blockchain (CEX withdrawals and ren bridge outputs)
- Crossing the ren bridge to find the associated ETH activity
- The majority of flows originated from addresses receiving 100 ETH outputs from Tornado Cash
- One bridged BTC output address was funded by an ETH address that received ETH for gas funding from the hacker’s address
- One “obvious mistake” was found, linking unmixed token activity to bridged BTC outputs to funds originating from an address disclosed by Liquid Global.
- Having identified the links to the Liquid Global hack, we completed a volume and timing analysis on the associated mixed BTC.
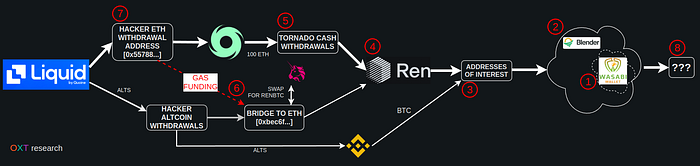
A schematic overview of the attribution path is provided below.
THE STARTING POINT
We introduced the custodial tumbler blender.io in our report on the Kucoin hack. In the report we detailed the tumbler’s abuse of Wasabi coinjoins in an attempt to obfuscate the tumbler’s activity.
With the Liquid Global hack, we anticipated a repeated use of blender.io in laundering of the stolen Liquid Global funds and picked up the trail searching for the hack related flows by searching for abnormally large flows into Wasabi coinjoins.
THE BRIDGE
Backtracking the large Blender inflows led to outputs sourced from Binance withdrawals and the renBTC bridge between ethereum and BTC.
Users that only have access to public block explorer tools can easily track flows across the ren protocol bridge from ETH to BTC. The ren burn transaction data fields include a UTF-8 encoded version of the BTC destination address.
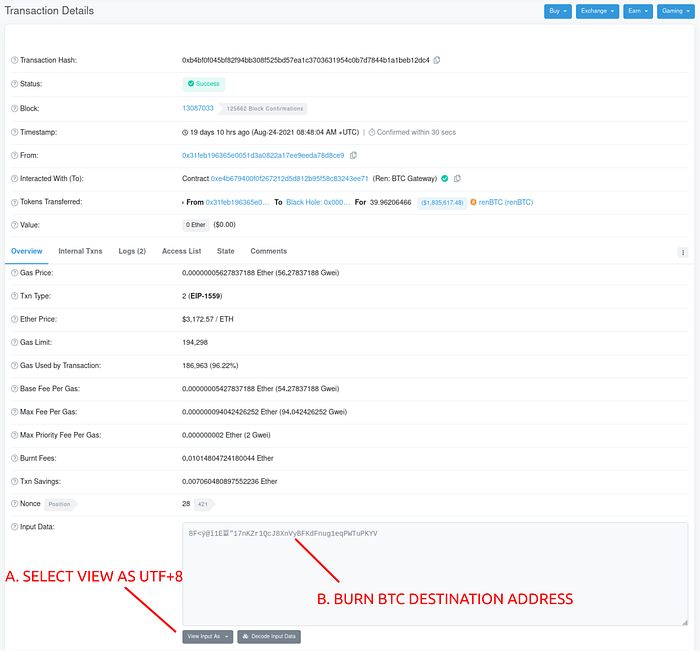
BTC to ETH “SMOKING GUN”
With the majority of ETH based assets entering Tornado Cash, linking the BTC related mixer inflows would require a volume and timing analysis (probabilistic analysis) on the related Tornado Cash outputs.
However, this hack has a “smoking gun” that deterministically links renBTC bridged outputs to the original hacker ETH withdrawal address. This link is summarized below.
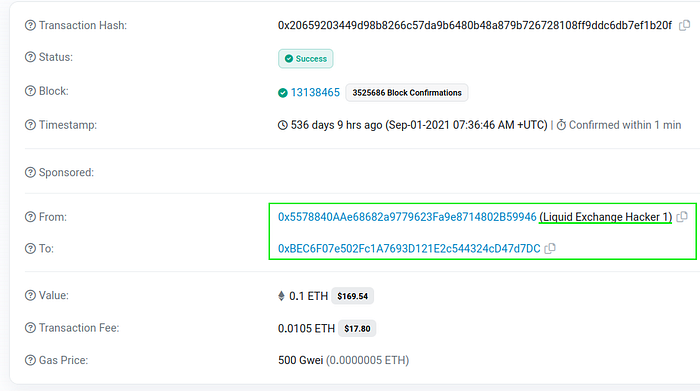
Our analysis found that [0x55788…] (Liquid Exchange “Hacker”):
- was used to send ETH for network fees to address [0xbec6f…] via this transaction
- [0xbec6f…] was used to bridge Energy Web Tokens, an altcoin reportedly stolen from Liquid Global during the hack
- The wrapped EWT was swapped on Uniswap for renBTC
- and the ren bridged to BTC address [1Fx1bh…]
A detailed analysis of the associated ETH activity is beyond the scope of this report, though several examples of ETH to renBTC address flows are shown in Sheet 1 of the attached spreadsheet.
BTC ADDRESSES AND ACCOUNTING
Table 1 below includes accounting of the majority of the Addresses of Interest. These addresses were either reported by Liquid Global in their blog post or discovered via their renBTC to Wasabi coinjoin flows associated with the hack ETH address.
Table 1 — BTC Address of Interest Overview
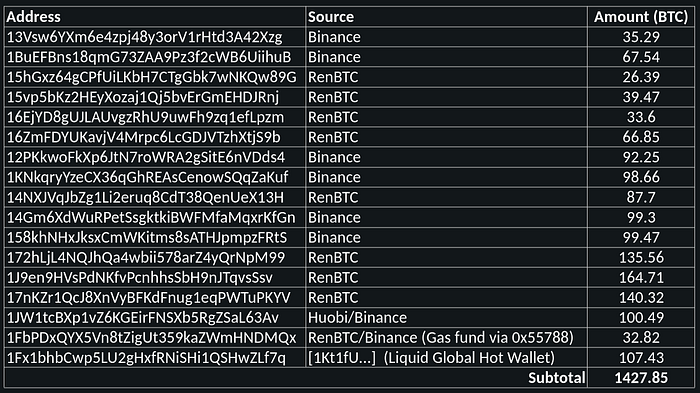
Accounting checks on these totals:
- Our estimates total about 1428 BTC which is valued at approximately $61.7 million (at the time of writing).
- The remaining token/ETH balance of the reported ETH addresses of interest [0x55788…, and 0xefb33…] is valued at approximately $11.3 million.
- A reported $17.4 million in stable coins were reportedly frozen (see 20 August update).
- Our subtotal USD value is approximately $92.7 million which brings our accounting roughly in line with the original reported $91 million in stolen funds.
BTC POSTMIX ATTRIBUTION
The majority of the spends the addresses noted in Table 1 follow the same process. The fingerprint of each wallet is detailed in Table 2.
Note: While the relationship between outputs on the blockchain cannot be disputed, the pseudonymous nature of bitcoin addresses adds uncertainty about who is responsible for spending an output. Wallet fingerprinting can be used as a sign that a new software (and possible user) are now involved in an observed transaction flow.
Table 2 — Wallet Fingerprints of Associated UTXO Flows
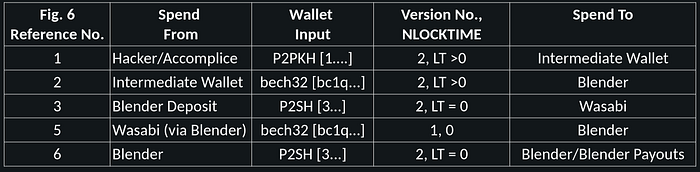
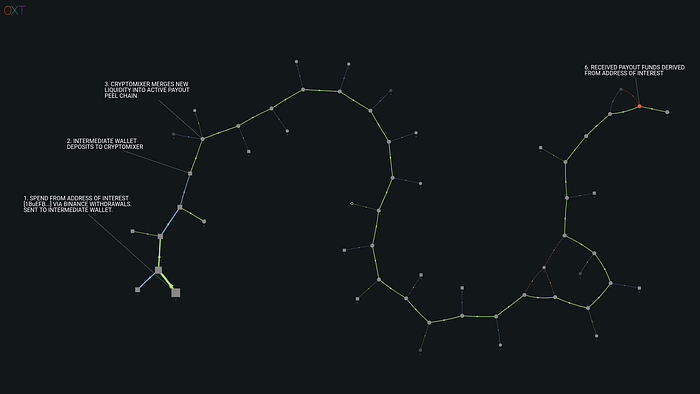
These UTXO flows are similar to those noted in our analysis of the KuCoin hack, with one small difference, the use of an “Intermediate Wallet” between the Hacker/Accomplice wallet and Blender deposit.
An annotated example of these observed flows is shown in the transaction graph below.
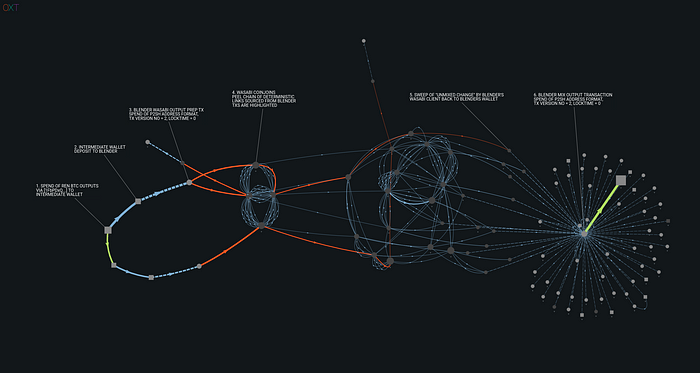
The above graph shows the BTC transaction flow history of unmixed tokens originating from the ETH blockchain, via address [1FbPDx…].
RECEIPTS — REVISITING BLENDER
Blender’s tumbler algorithm is more discrete than other well known tumblers such as Chipmixer. Blender’s algorithm:
- does not have a static cluster to observe
- does not reuse addresses and
- does not create transactions with an equal output footprint
Without these, evaluating Blender requires a “graph traversal” analysis that follows inputs and outputs from transactions with the same wallet fingerprint as Blender.
This analysis is susceptible to high amounts of false positives and subsequent collapse of the adjacent transaction graph. Intermittent “checkpointing” to verify Blender’s status and recent transactions are also required to keep tabs on the state of the tumblers UTXOs.
During the tracking of the Liquid Global hack funds we anticipated the hackers/accomplices use of Blender and began interacting with Blender at the same time as funds associated with the hack were exhibiting patterns similar to the laundering process used in the processing of funds from the KuCoin hack.
LETTERS OF GUARANTEE
Custodial tumblers take possession of user’s funds. By taking possession, they present users with a risk of loss of funds. Loss of funds may occur for several reasons including:
- visiting phishing websites
- attacks on website/user security such as SSL stripping
- bugs in the tumbler software
- tumbler exit scams (deliberate theft of user coins)
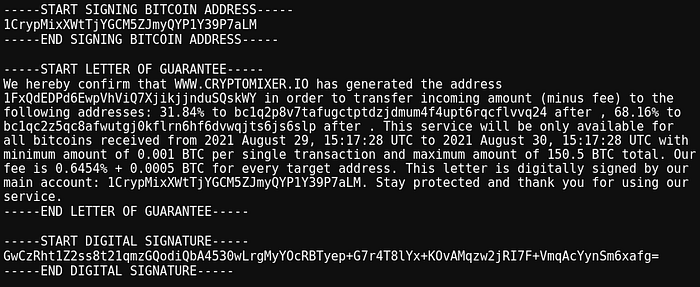
To alleviate these concerns, tumblers will issue a “Letter of Guarantee” with each initiated mix. These letters are signed with the tumbler’s BTC “service address”, a private key controlled by the tumbler’s admin. A Letter of Guarantee acts as a kind of chain of custody that shows cryptographic proof of ownership of the tumbler deposit address and intended payment to the user withdrawal address.
If a user has an issue they can submit the letter of guarantee to support staff in order to receive their intended output. Users can also use these letter’s of guarantee to prove provenance of funds.
Subsequently, these letters can be used as cryptographic evidence for verification of our observations.
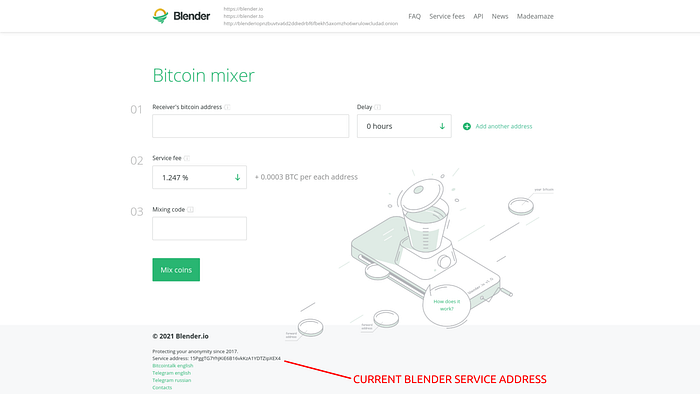
TUMBLERS UNDER THE HOOD
Custodial tumblers effectively function as “coin swap” services.
Where users deposit coins with a certain history, and hopefully receive coins with a different history in return. When a user interacts with a tumbler, they can never know the history of their payout until they receive them.
This trait is associated with the original concepts of “taint”, where users of custodial tumblers received payouts with histories associated with “nefarious” activity and later found themselves in trouble with their centralized exchange or incorrectly accused by law enforcement.
This unpredictable nature of tumbler output history can also make it difficult for analysts looking to document specific tumbler activity and often requires repeated attempts to identify the observed behavior.
While evaluating blender during the tracking of the KuCoin hack, we received outputs with a several unique histories. The two most important output histories are discussed below.
The first was sourced immediately from a 0.8 BTC Wasabi mixed output. It is a rare occurrence that normal users spend these outputs because they have anonymity sets below the default enforced by Wasabi wallet.
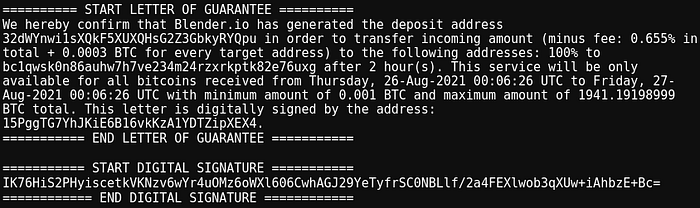
We found that our output was deterministically sourced from a Blender transaction, indicating that funds from Blender were present in the mix responsible for processing our Blender payout.
In another case, we received an output that was not mixed with Wasabi but originated several hops from an address of concern [172hLj…]. The receipt for this transaction is shown below.
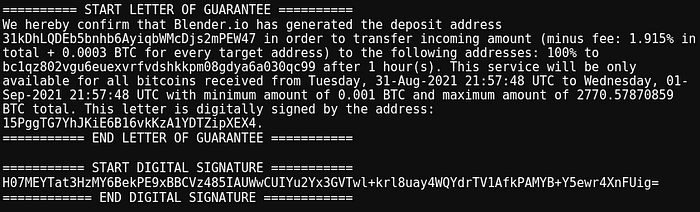
The transaction graph showing the associated flows is provided in Fig. 10 below.
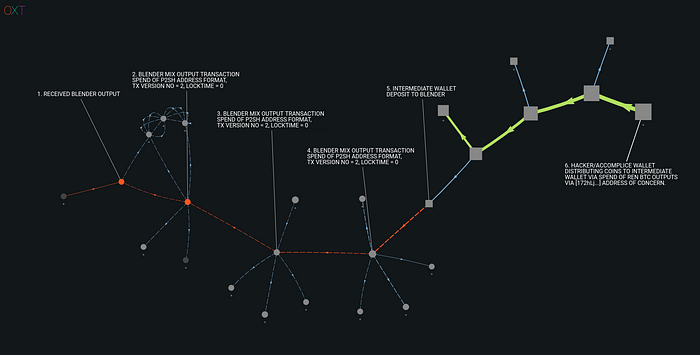
The conclusions that can be drawn from the observations from our interaction with Blender are as follows:
- Blender is abusing Wasabi coinjoins in an attempt to hide its activity
- The Liquid Global hackers/accomplices are using Blender to obfuscate their transaction history
THE MISSING PIECE OF THE PUZZLE — CRYPTOMIXER.IO
Most of the coins from the second half of the addresses in Table 1 were mixed through Blender.
However in several cases portions of the BTC spent from the Address of Interest List were sent to a P2PKH addresses (an address formats that start with a [1…]). These addresses indicate the use of a different tumbler other than Blender which uses P2SH format addresses that start with a [3…].
The spends from the P2PKH addresses were merged into long peel chains.
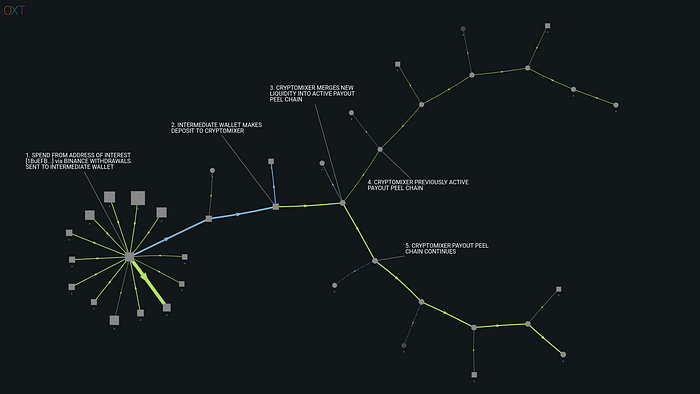
We first observed this pattern during tracking of funds stolen from the November 2020 Exmo hack (another forgotten hack). This pattern was also present in the later stages of our analysis of the 2020 Kucoin hack.
Seeing as this has been a recurring pattern, we set out to find the entity responsible.
And it wasn’t long until we discovered cryptomixer.io.
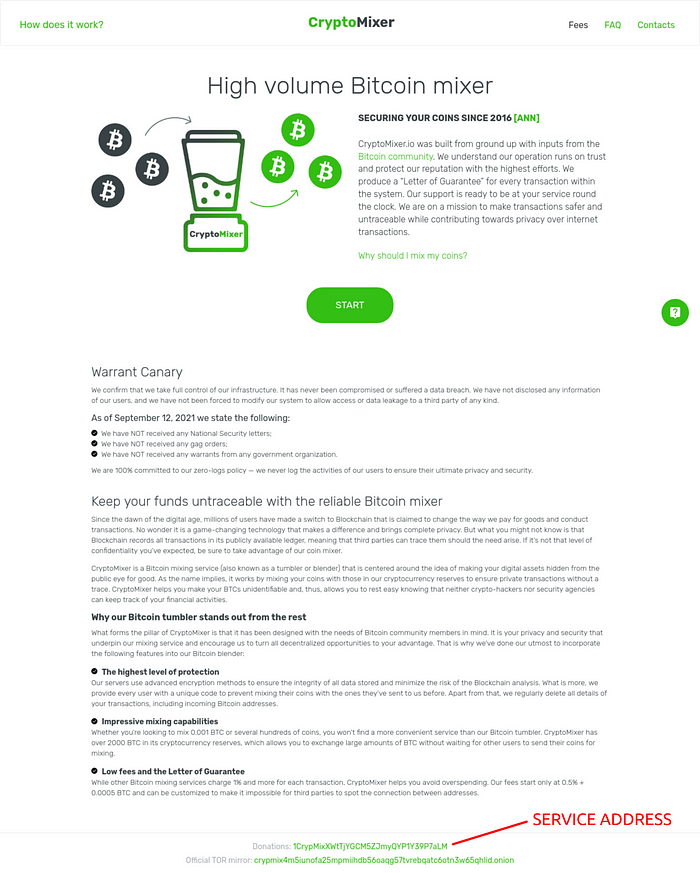
CryptoMixer has a relatively simple tumbler algorithm. Payouts are made from long “peel chains” typically with the following characteristics:
- Transactions with 1 input and 2 outputs
- Input and change address script type: P2PKH
- Transaction payment output position: 0 (Constant)
- Transaction change output position: 1 (Constant)
- Version No.: 2
- Locktime: >0
A single CryptoMixer peel chain’s transaction graph activity is easily tracked with a naive hard-coded traversal script thanks to the tumbler’s lack of randomness.
Generally, as the CryptoMixer peel chain balance dwindles during payout operations:
- The remaining funds are either “swept” in a transaction with no change output which terminates the peel chain; or
- Funds from a previous tumbler deposit are combined with a previous peel chain output and the process continues.
Anticipating a replay of the long peel chain activity observed during laundering of the coins from the KuCoin and Exmo hack, we began interacting with the tumbler while funds from the Liquid Global hack began spending to possible P2PKH CryptoMixer deposits addresses.
This allowed us to “checkpoint” the current state of the CryptoMixer wallet and payouts.
Similar to our experience with Blender above, our CryptoMixer payout was sourced from a peel chain funded with an outputs from Binance that has been included in our address of concern list.
ATTACKING THE TUMBLERS
After identifying the use of Blender and CryptoMixer, we set out to complete another volume and timing analysis searching for postmix activity attributable to the Liquid Global hack.
Below is a high level overview of our process for identifying postmix transactions sourced from the Liquid Global hack:
- Analyze the premix activity and build a list of deposits to Blender and CryptoMixer and establish the deposit time window.
- Analyze the activity of Blender with a graph traversal script with the goal of confirming that stolen funds were a large part of Blender’s activity during the approximate deposit time window.
- Check large volume postmix spends sourced from Blender during this period to identify recurring postmix spending patterns.
- List all withdrawals matching this pattern.
- Verify that the timeline of the deposit/withdrawals is valid (balance should never be negative/at least not a large negative value)
- Use the postmix transaction graph to identify transactions coming from CryptoMixer.
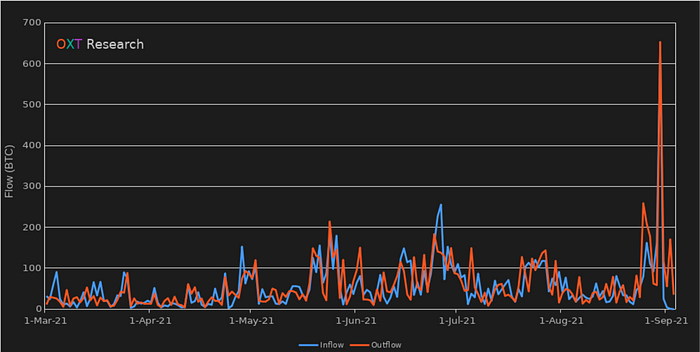
During our timeframe of interest, Blender saw a significant spike in activity. A complete list of Blender transactions and supporting documentation used in this analysis can be found below.
Blender’s daily BTC inflow and ouflows tend to range between 50 and 100 BTC per day. During the inflows from the Liquid Global Hack inflows and outflows spiked significantly to spiked to over 200 and 600 BTC.
The large volume postmix spending volume spikes observed during this analysis typically followed this process:
- Consolidation of mixed output for exactly 50 BTC to address [32P5GP…] (example TxID).
- 50 BTC inputs from [32P5GP…] are then consolidated into 100 BTC UTXOs
- Second consolidation of multiple 50 BTC inputs from [32P5GP…] to [3Gs9Fp…].
- From [3Gs9Fp…], spends are made to several addresses [1DqPbz…, 1Crhhc…, 1DwszG…, ] controlled by the exchange zb.com.
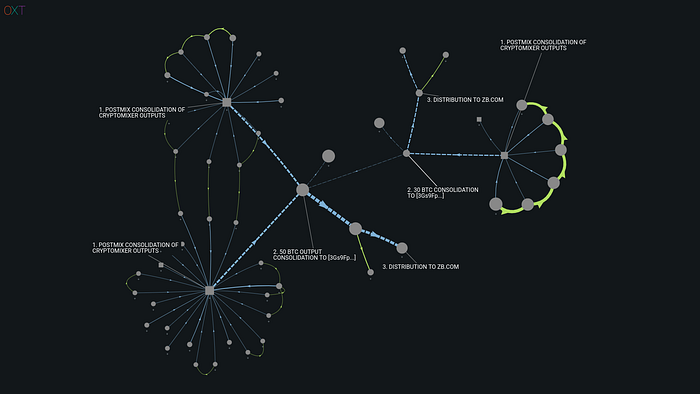
Address [32P5GP…] and zb.com are clearly the focal point of this large volume postmix activity, receiving well over 1000 BTC during the relevant time period.
We also noted a secondary large volume postmix pattern consolidating mixed outputs from both Blender and CryptoMixer to address [1NbiXJ…].
This address receives another 450 BTC from both tumblers that is spent to Huobi address [15qRSE…], an address we first noted in our previous report on the DPRK “conspirators”.
We believe both address and [32P5GP…] and [1NbiXJ…] received a significant majority of the funds related to the Liquid Global Hack.
A complete list of deposits from the Addresses of Interest to Blender and CryptoMixer as well as “most likely” withdrawals are included in the attached spreadsheet.
SUMMARY
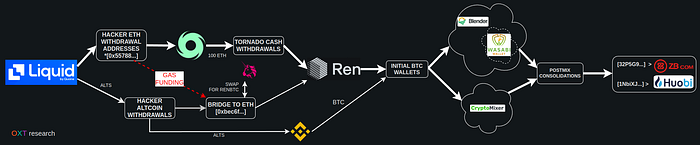
- Theft of assets from Liquid exchange
- Mixing of ETH assets with Tornado Cash
- Swapping of altcoins on Binance or DeFi exchanges
- Bridging of ETH assets to BTC blockchain via ren BTC bridge
- Mixing of BTC with Blender and Cryptomixer
- Consolidation of mixed outputs to and [32P5GP…] and [1NbiXJ…]
CONCLUSIONS
Over our last several reports, we have been evaluating the use of several custodial tumblers in the attempted laundering of large volume exchange hacks.
From our observations we can conclude the following:
- Custodial tumblers without address reuse or static clusters present unique challenges for tracking and evaluating mixer activity.
- These tumblers require repeated interaction to “checkpoint” and establish known activity. From this interaction, the general tumbler algorithm can be evaluated and the past/future spending tracked with graph traversal analysis.
- Our identification, descriptions, and interactions with CryptoMixer and Blender can be used to better evaluate the attempted laundering of funds from future thefts.
- Based on similarities in mixing patterns between the 2021 hack of Liquid Global and the 2020 hack of KuCoin, the same entities are likely responsible for both hacks.
- The pseudonymity of bitcoin and any non-readily apparent spending patterns must be considered by analysts. Simply because funds associated with a hack enter a tumbler or coinjoin process does not imply that “the hacker is using service X”. Intermediate wallet fingerprints should be considered in these contexts as they may represent new wallets, users, or services handling the associated funds.
- From our volume and timing analyses, the postmix spending from the Liquid Global is most likely associated with [32P5GP…] and [1NbiXJ…] before sending to zb.com and Huobi, respectively. The spending from these addresses should be used as a follow up to continue the evaluation of the Liquid Global Hack.
