The KuCoin Hack
Introduction
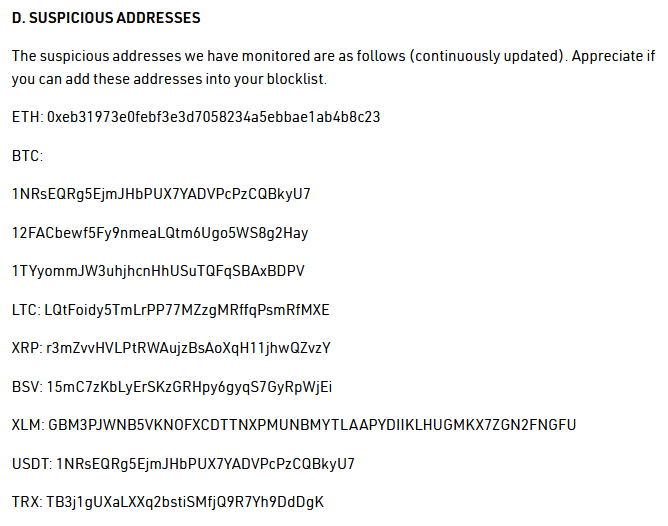
On September 26th 2020, KuCoin, a Hong Kong based cryptocurrency exchange suspended withdraws as part of an on-going "security incident". Shortly after the event, KuCoin revealed their security had been compromised and funds from several crypto hot wallets had been withdrawn to a list of suspicious addresses. The stolen crypto was valued at approximately $280 million at the time of the hack.
1008 BTC, valued at approximately $11 million, was among the reported stolen crypto. These coins remained unspent until late October.
Shortly after the incident, most of the stolen altcoins began spending from the noted addresses. On November 11th, almost 2 months after the incident, a tweet thread from the KuCoin CEO stated that 84% of the stolen cryptocurrency ($235M of $280M) had been recovered.
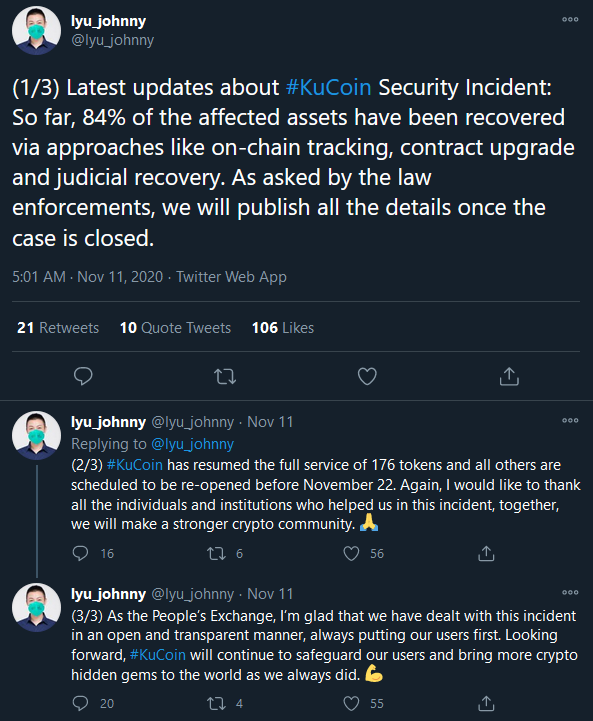
Specifics on which assets have been recovered are relatively vague. According to a news report by CoinJournal.net, the stolen altcoins seem to make up the bulk of the recovered assets.
Based on the reported recovered volumes, the timing of the recovery news, and our observations of the movement of the stolen BTC, we do not believe that the BTC was among the recovered assets.
Executive Summary
The immediate spending patterns of the stolen BTC have been well documented. Due to the usage of several mixers, the flows and destination of the stolen BTC remains largely undiscussed by the community. In this report, we aim to provide some clarity on the situation by discussing the following:
- Details of the immediate flows of the 1008 stolen BTC.
- Identification of several mixing services used to obfuscate the flows of the stolen BTC.
- Testing and refining a volume and timing analysis for evaluating likely postmix UTXOs attributable to the stolen coins.
- A discussion of the postmix spending patterns of our likely UTXO list.
- Mixing services as only a small part of an elaborate obfuscation scheme.
- Possible attribution of the entities involved in the massive scheme.
The Flow of Stolen BTC
A high-level timeline of the flows of the 1008 stolen BTC is provided below:
- 25 September 2020
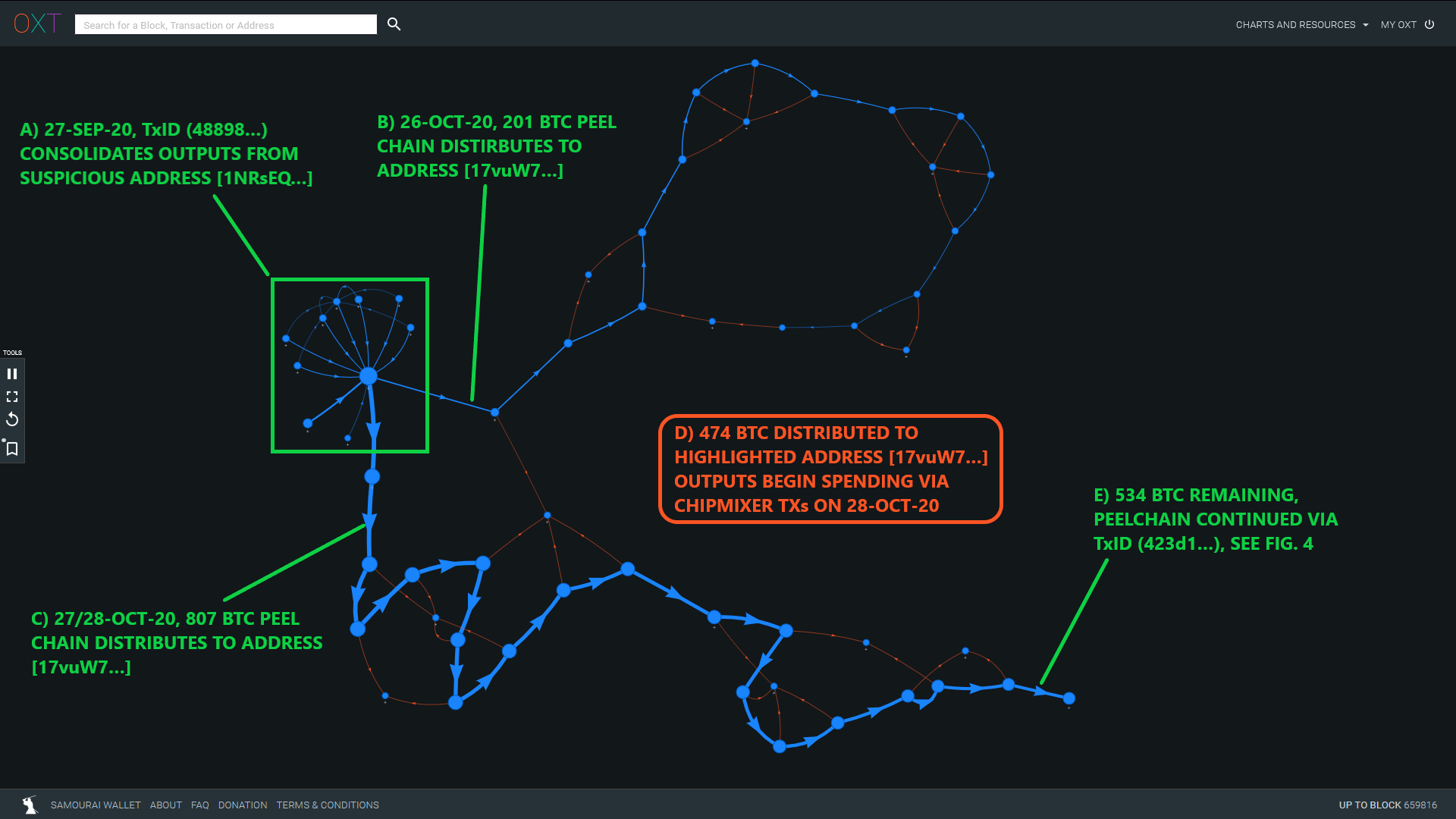
The stolen coins are spent to address [1NRsEQ...] over a series of 9 transactions as a part of the security breach. - 27 September 2020
The 1008 BTC is split into two UTXOs, one for 201 BTC and another for 807 BTC, via TxID (48898...). - 26 - 28 October 2020
Approximately 474 BTC are spent to a single address [17vuW7...] over a series of transactions. Outputs from this address are later consumed in ChipMixer transactions. - 30 October - 2 November 2020
The remaining roughly 534 BTC are distributed to an "intermediary" wallet receiving to nested P2WPKH addresses. - 31 October - 3 November 2020
The intermediary wallet begins spending to bech32 address formats. All UTXOs are "partially mixed" through Wasabi Wallet CoinJoins. - 3 November 2020
"Unmixed" change outputs and de-anonymized mix outputs begin flowing from Wasabi to apparent "large consolidation transactions" receiving large volumes from nested P2WPKH addresses. For now, we will refer to this as the "post-Wasabi wallet."
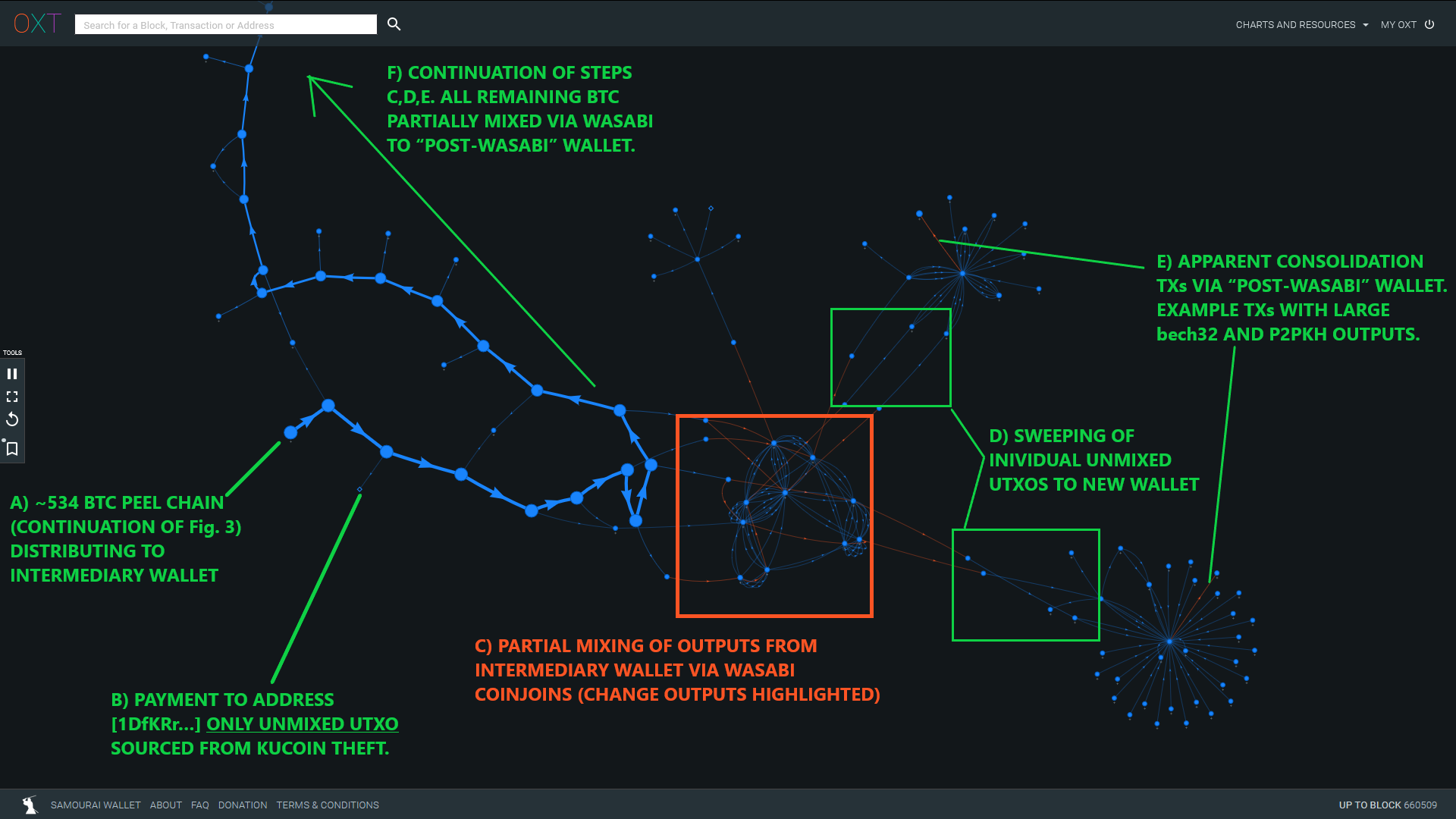
An example of these flows is illustrated below in Fig. 4. A detailed timeline of these flows including premix distributions to each mixer and tracking of the major Wasabi CoinJoin change outputs can be found in the resource spreadsheet (Tabs 1 and 2).
The flows from the suspect addresses into the mixing services are deterministic, or mathematically certain.
We know that 474 BTC were mixed via ChipMixer.
We know that the remaining 534 BTC were mixed via a different, more complex process. This process needs further investigation, but we begin to explore the possibility that we are observing a second custodial tumbler.
The flows out of the mixing process are not deterministic and offer unique challenges to analysts. In the remainder of this report we develop a series of hypotheses for testing and identification of possible postmix UTXOs attributable to the original KuCoin theft.
We attempt to invalidate each hypothesis in a fashion typical of the scientific method. If the observed data does not invalidate our hypotheses, we continue refining our approach in an effort to develop a "most likely" postmix UTXO list.
Background Knowledge
Bitcoin wallets generate transactions with additional metadata that can be used to "fingerprint" the software (or "wallet") used to create a transaction.
We used wallet fingerprinting to identify the unique wallets used in the flows of the stolen KuCoin BTC displayed in Figures 3 and 4.
Common transaction fingerprint metatdata includes the following:
- Address type used for inputs and outputs.
- Batch spending (indications of service activity) vs. simple spending (indications of single user activity).
- Change output indexes (VOUT 0 vs. VOUT 1) for simple spends.
- Transaction Version Number and Locktime.
Analysts tracking the flow of bitcoins can use transaction fingerprinting to note coins entering a new service or being spent by new wallet software.
In our analysis of the flows of the stolen KuCoin BTC, we noted several unique fingerprints used to construct the transactions involved.
A summary of each wallet, and their unique fingerprints are shown below in Table 1.
| Wallet | Input Address Type | Output Address Type | Denomination Fingerprint | Version No. | Locktime |
|---|---|---|---|---|---|
| Stolen Fund Wallet | P2PKH (1...) | P2PKH (1...) | None | 2 | Blockheight |
| ChipMixer | P2PKH (1...) | P2PKH (1...) | "Chips" (0.001, 0.002,... 8.192 BTC) | 2 | Blockheight |
| Intermediary Wallet | Nested P2WPKH (3...) | No change, possible self-spend | None | 2 | 0 |
| Wasabi Wallet | bech32 (bc1q...) | bech32 (bc1q...) | Identical outputs (Coinjoin Footprint) | 1 | 0 |
| Post Wasabi Wallet | Nested P2WPKH (3...) | Nested P2WPKH (3...) | None | 2 | 0 |
Stolen Fund Wallet Fingerprint (critical in later part of analysis)
- P2PKH address types for inputs and "change" outputs
- Transactions created with a Version No. 2
- Locktime = current block height
ChipMixer
- A unique footprint that can be found relatively easily by scanning the blockchain for similar transactions
Intermediary Wallet & post-Wasabi Wallet
- The fingerprint of the Intermediary and post-Wasabi wallet are identical
Custodial Tumblers
Custodial tumblers were among the first privacy techniques employed by BTC users attempting to obfuscate their bitcoin transactions. Recently the term for tumblers, mixers, and coinjoins has become interchangeable. We tend to use "mixer" as a general term to describe both obfuscation techniques. Despite this confusing of terms, there are major differences between custodial tumblers and coinjoins.
The purpose of custodial tumblers is to act as a swap service. Users deposit coins to the tumbler and (hopefully) receive different UTXOs with a new transaction history in return. This swapping process results in a "broken" transaction graph that severs the link between a user's deposits and withdrawals. To prevent users from receiving their original deposits, custodial tumblers keep BTC "reserves" to supply liquidity during times of high demand.
Frequently, users interacting with custodial tumblers are attempting to hide the movement of coins sourced from illicit activities. The swapping nature of custodial tumblers and proximity to inflows from illicit activities means a user may receive "tainted" coins in return for their deposit. "Taint" risk is an inherent risk present in the process of swapping coins with unique attributable histories. In contrast, a true Zerolink CoinJoin provides sufficient plausible deniability against evaluating a UTXOs unique history and therefore its "taint".
The "Ideal" Custodial Tumbler
- Opaque
Operates a "shared" wallet, with an internal database. - No Links
Users deposit funds into the shared wallet and receives "new coins" that are not linked to their original deposit. - No Cluster
No wallet cluster detected by traditional clustering algorithms. - No Footprint
Minimal footprint with irregular input and output denominations. - No Exit Scam
Does not exit scam with user deposited funds.
Attempts to track the swapping of funds across tumblers is heavily reliant on volume and timing analysis.
Evaluating ChipMixer
Due to the loss of fund risks and normal user spending habits, users often keep their coins in the custody of the tumbler for relatively short periods of time. This general behavior leads us to the following hypothesis:
Hypothesis: The KuCoin hacker will minimize the amount of time their BTC is kept in the custody of the custodial tumblers.
ChipMixer transactions are easily identifiable due to their standard denomination output footprint (chips). Chip denominations are 2x multiples of 0.001 BTC and range up to 8.192 BTC.
We scanned each bitcoin transaction between early August and late November for a fingerprint matching ChipMixer transactions. This list is compiled in the attached ChipMixer Transaction List CSV file. From there we compiled the results to evaluate daily inflow and outflows.
Recall that 474 BTC sourced from the KuCoin hack were deposited into ChipMixer in the following manner:
- 26 October 2020
201.0 BTC - 27 October 2020
148.4 BTC - 28 October 2020
125.0 BTC
The daily outflows from ChipMixer is shown in Fig. 6 below.
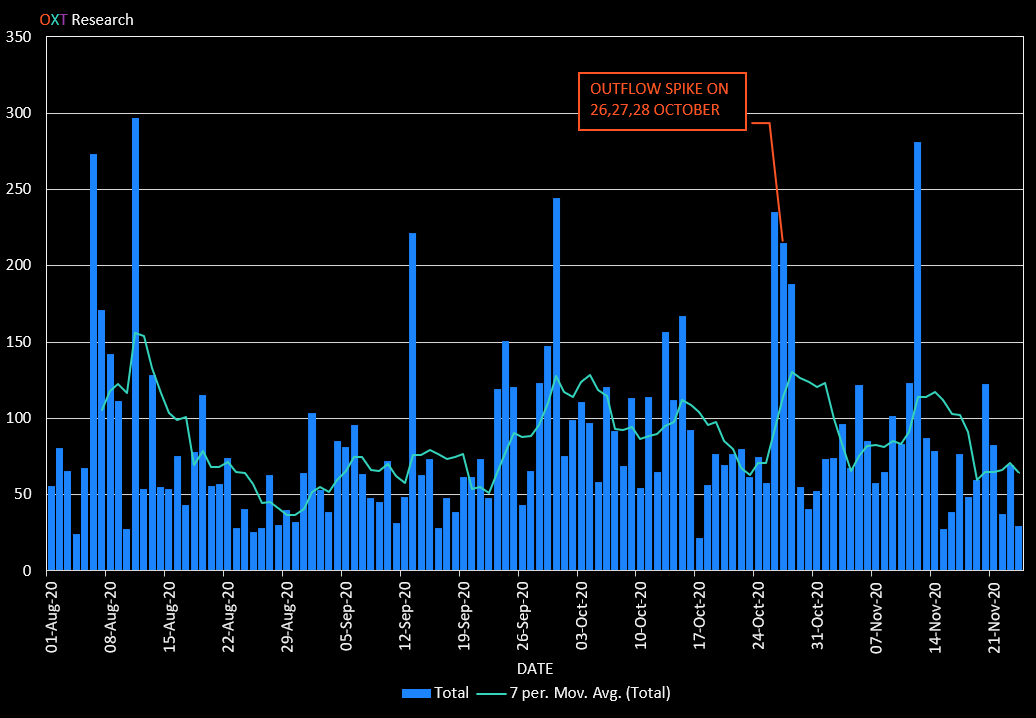
Recent daily outflows from ChipMixer average around 85 BTC per day with occasional spikes to more than 150 BTC.
An outflow spike corresponding with the KuCoin stolen inflow amounts occurred on 26, 27, and 28 October.
This spike is likely an indication confirming our hypothesis that the KuCoin BTC would only remain in ChipMixer's custody for a short period of time.
Combining Volume and Timing
A postmix wallet composition with a large number of UTXOs can make safe postmix spending difficult. 20 to 30 mixed outputs tends to be manageable for most users. Having mixed 474 BTC with ChipMixer, a 20 to 30 mixed output count would result in outputs ranging from 15 to 25 BTC.
Hypothesis: The KuCoin hacker will tend to receive a disproportionate amount of large mix outputs from the relevant ChipMixer time frame.
A histogram showing the postmix spending patterns for ChipMixer between August and late November are shown below.
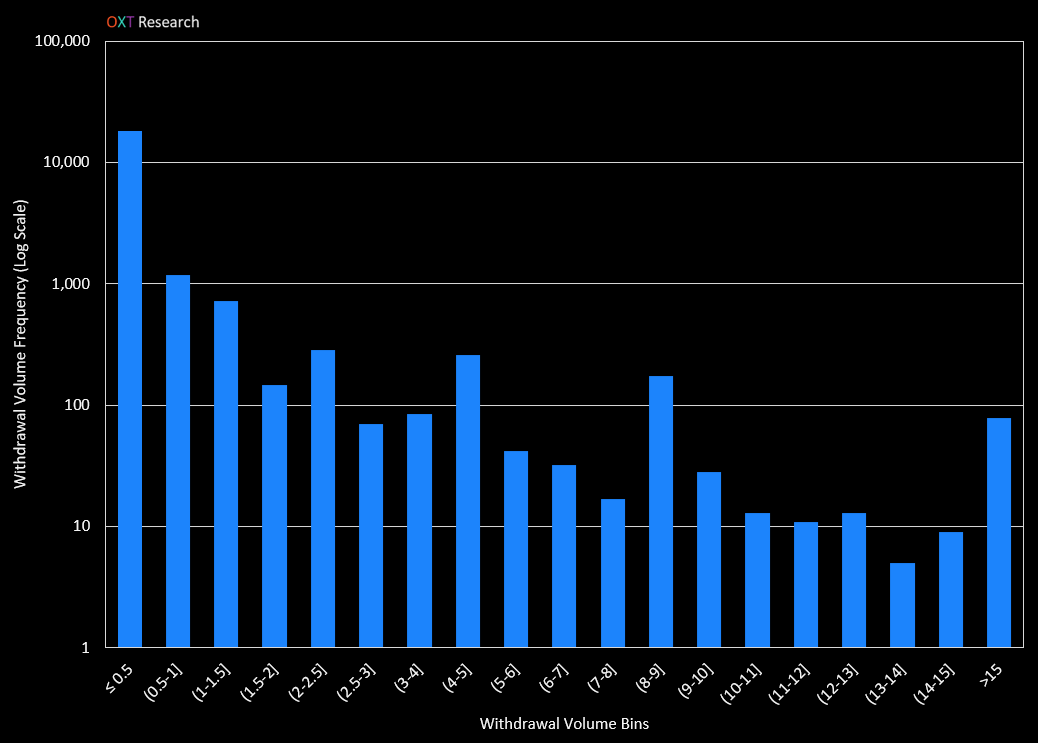
Of the 21,200 withdrawal transactions between August and late November, over 16,700 are for less than 0.5 BTC. This is consistent with most users normal spending patterns.
Postmix spends greater than 1.5 BTC are extremely uncommon, on the order of 12% of total postmix spends for the considered timeframe.
If the hacker's postmix UTXO size followed our presumptions above, their outputs will be relatively rare.
Filtering outspends from ChipMixer for the 26, 27, and 28 October time frame that spend 8.192 BTC or more, results in only 27 postmix transactions (see resource spreadsheet - Tab 3).
A breakdown of inflows and outflows for this timeframe are shown below in Table 2.
| BTC Flows | 26-Oct-20 | 27-Oct-20 | 28-Oct-20 |
|---|---|---|---|
| Deposits - Total | 244.5 | 176.1 | 151.2 |
| Deposits - Sourced from KuCoin Hack | 201.0 | 148.4 | 125.0 |
| Deposits - KuCoin Hack % of Total | 82% | 84% | 83% |
| Withdrawals - Total | 235.1 | 215.1 | 188.3 |
| Withdrawals - 8.192 BTC or Greater | 198.5 | 174.6 | 145.4 |
| Withdrawals - 8.192 BTC or Greater % of Total | 84% | 81% | 77% |
The KuCoin hack deposits and large withdrawals represent over 75% of the daily inflow and outflows.
If the hacker withdrew their funds on the same days as their deposits, this implies that at least some of their large withdrawals were among those occurring during this time frame.
This volume and timing analysis is not definitive, but provided us with a short list as a starting point for further refining our hypotheses and postmix UTXO list.
We have still not covered the possibility that these large withdrawals were performed by another entity.
Given that the goal of a custodial tumbler is to swap coins with different histories, we can create a two-hypothesis scenario for who may control the large outflows that occurred during the 26, 27, and 28 October timeframe.
Hypothesis 1: The hacker withdrew shortly after making their deposits.
Hypothesis 2: Another entity was waiting for incoming liquidity before making their large withdrawals..
If the second hypothesis were true, we would expect to see a large volume of withdrawals from KuCoin deposits sourced from address [17vuW7...] during the noted timeframe.
This was not the case. The majority of the large volume transactions from 26 and 27 October were not sourced from the KuCoin deposits, but that changed on 28 October.
In fact, the hacker ceased deposits to ChipMixer on 28 October, was this in response to receiving the coins they had originally deposited on the 28th?
Since a significant majority of the large withdrawals from the 27th and 28th were not sourced from the KuCoin deposits, we concluded that the hacker was in fact withdrawing their funds on roughly the same day.
Identifying The Missing Link
At first glance, the remaining 534 BTC is "partially" mixed through Wasabi CoinJoins. Partial mixing refers to the significant volume of "unmixed change" that exits the coinjoin process prior to "complete" mixing. These change outputs are deterministically linked (traceable) to the original UTXO that entered the coinjoin process.
Approximately 200 of the original 534 BTC that entered Wasabi CoinJoins from the KuCoin theft exited as "unmixed change".
Several mixed UTXOs were paid to reused "unmixed change" addresses and de-anonymized.
A list of the major partial mixing peel chains can be found in the resource spreadsheet (Tab 2). The "unmixed change" and mixed outputs are spent individually to a new wallet before apparent consolidation by another wallet. This process is depicted in Figure 2 and again in Figure 8 below.
An Unknown Mixer
We first identified a similar pattern of flows from an entity abusing Wasabi CoinJoins during our tracking of the "Lazarus Group Conspirators" allegedly responsible for laundering BTC on behalf of the notorious hacking group.
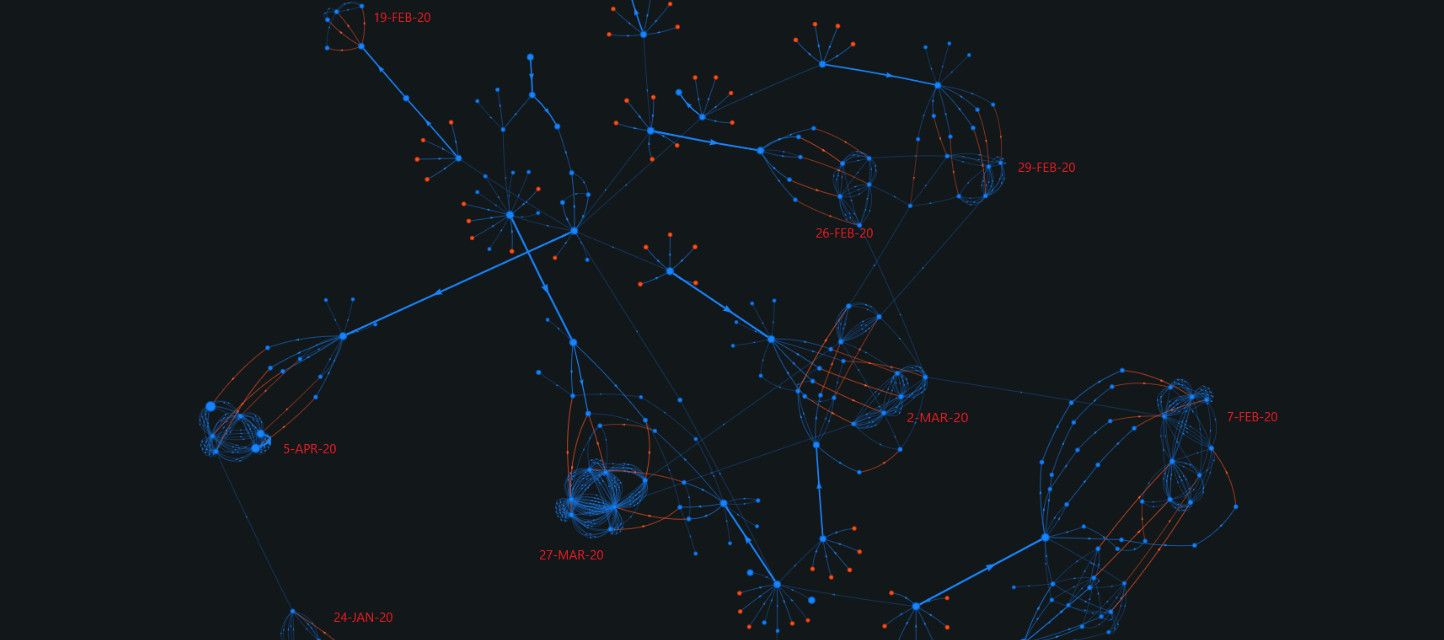
At the time, we noted a single (unlabeled) cluster responsible for large partial mixing volumes spent in an identical scheme to the KuCoin hack.
We have since labeled this cluster as Hydra Market, the largest and longest operational Dark Net Market, extremely popular in Russia and Eastern Europe.
During this investigation, we noted similar, smaller, and less direct outflows from Hydra Market that were used as inputs to the "intermediary" wallet with UTXOs from the KuCoin hack.
UTXOs sourced from Hydra were also used in transactions similar to the "post-Wasabi" wallet. An example of this behavior is shown in Fig. 8.
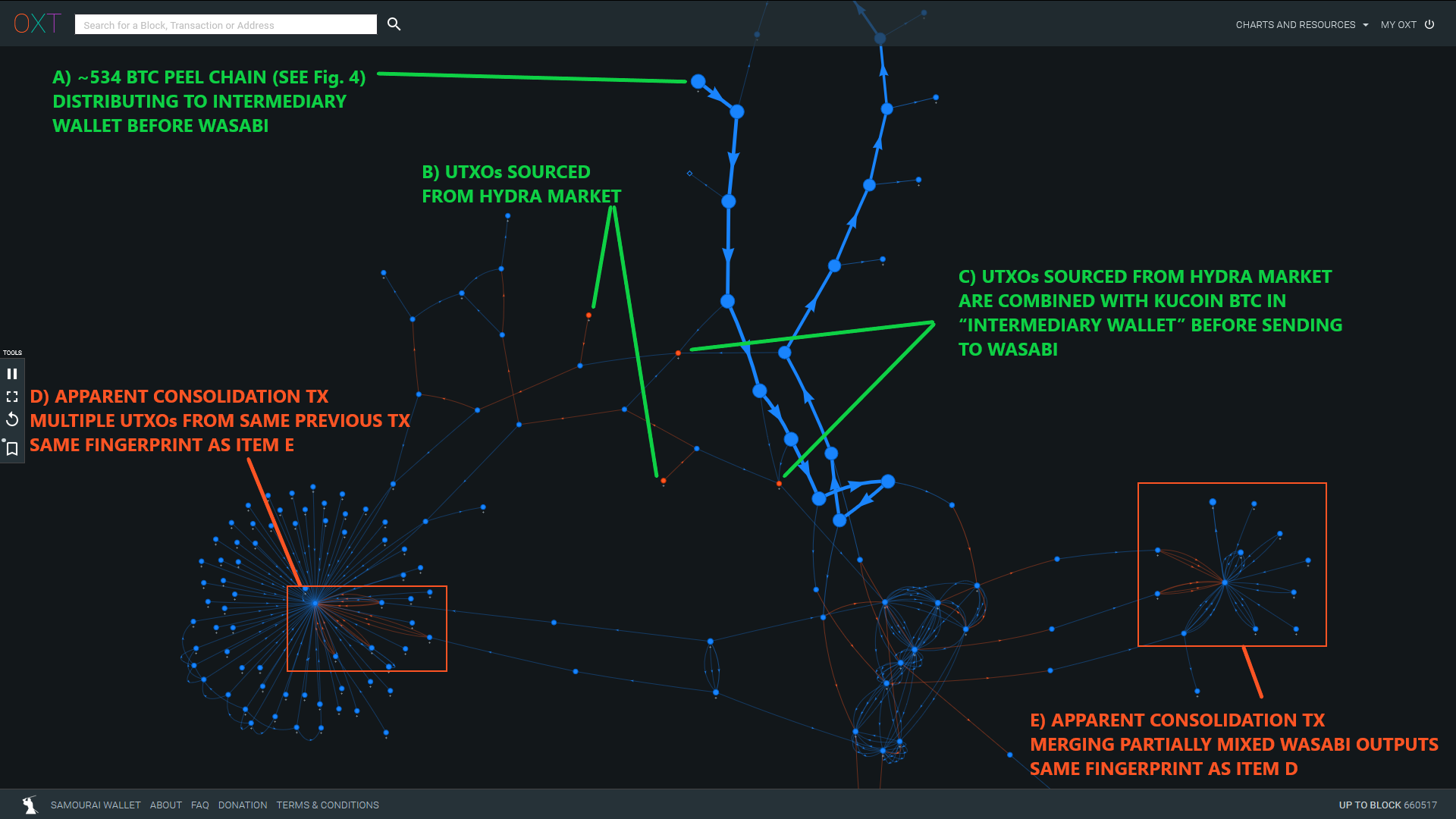
The transactions highlighted in Item D and E (TxIDs 976d0... and 04b51...) have the same fingerprint and possibly represent onchain activity from the same entity.
Consolidating multiple "split" outputs from the same previous transaction is generally more expensive than using a single UTXO in the next transaction. This is not "normal" spending behavior and is possibly indicative of an algorithmic tumbling process attempting to break up large amounts.
This graph only shows one example of proximity to Hydra Market, we noted several others in the premix transaction graph, indicating the observed entity is popular in eastern Europe and Russia.
Who are you Blender.io?
We used the above info to begin searching for the entity responsible for these possible tumbler transactions. It wasn't long until we stumbled on Blender as the entity responsible.
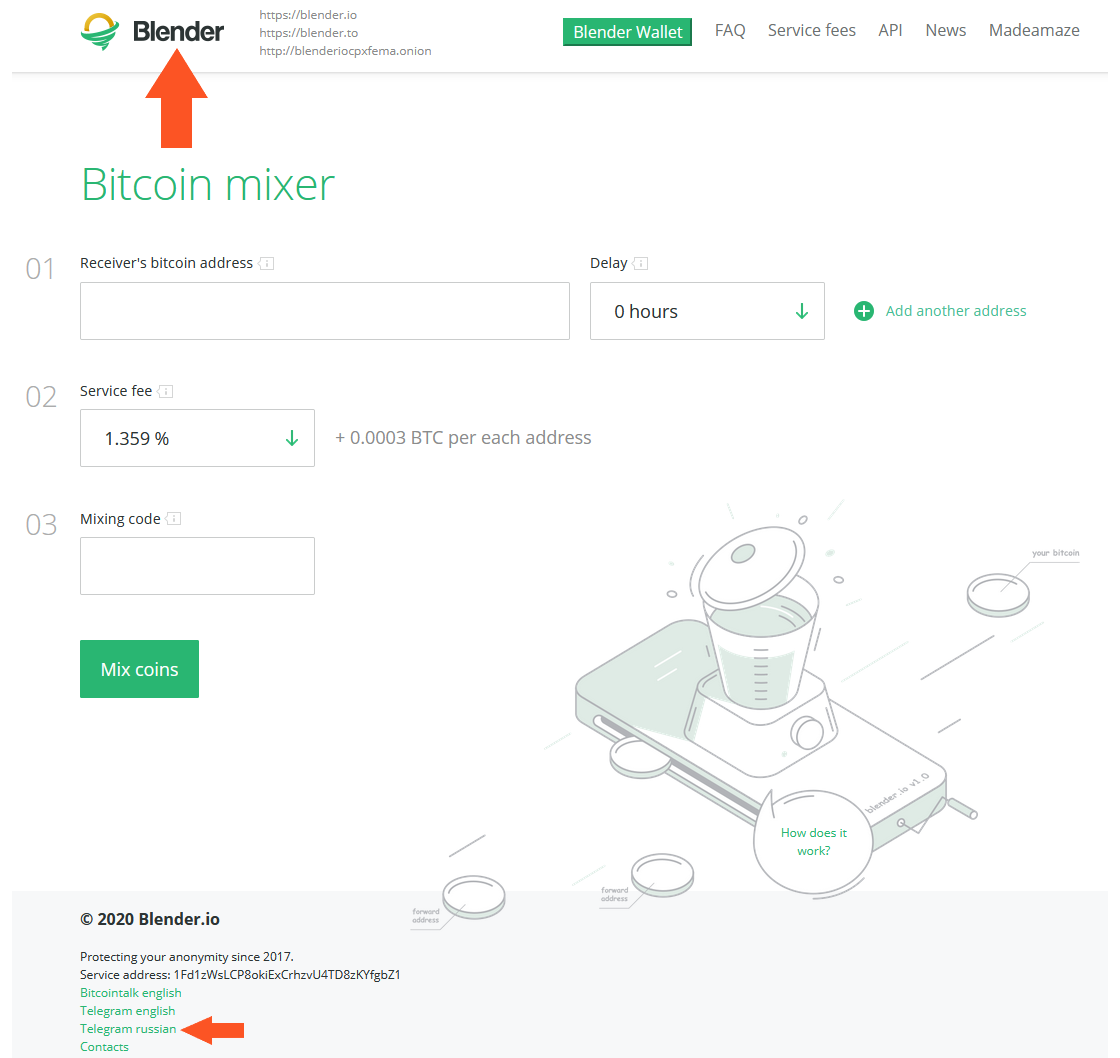
Our scanning of social media platforms revealed several public Blender transactions. These transactions had identical fingerprints to those noted during our tracking of the flows from the KuCoin theft (see Table 1 Intermediary and Post-Wasabi Wallet). We confirmed the Blender transaction fingerprint by sending coins through the tumbler. We even received a payout UTXO from the same close proximity transaction graph to the KuCoin BTC flows.
Our observations confirm that the observed Post-Wasabi Wallet transactions were performed by Blender.
Evaluating Blender
Having identified the service responsible for the Post-Wasabi wallet transactions, we analyzed the Blender transaction process in a similar manner to our evaluation of ChipMixer. This analysis required an added twist. Blender transactions do not have an output denomination footprint that allows for identification by scanning each transaction in a mined block.
Instead, we evaluated likely Blender transactions with a graph traversal heuristic by starting with several "seed" transactions identified by our manual analysis.
Our graph traversal heuristic followed the forward and backwards transaction graph of the seed transactions to identify transactions with the fingerprint for the Intermediary and Post-Wasabi wallet noted in Table 1.
The traversal was bounded by spends from separate entities and transaction fingerprints not meeting the noted pattern. The results of this heuristic are included in the attached Blender Transaction List CSV file. The transactions noted in Fig. 8 (TxIDs 976d0... and 04b51...) were identified by our heuristic.
After identifying a list of likely Blender transactions, we evaluated Blender's typical inflows and outflows, similar to the analysis for ChipMixer in Fig. 10.
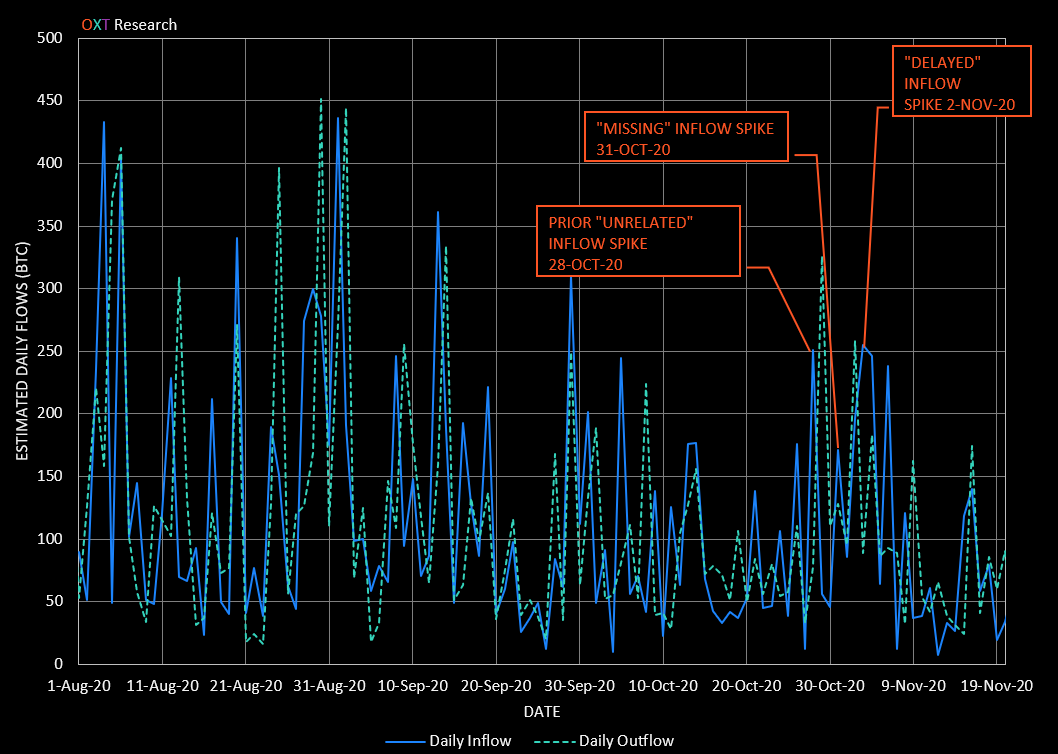
Recent daily flows from Blender average around 115 BTC per day with occasional spikes to more than 250 BTC.
Smaller inflow spikes occur prior to the KuCoin inflows. These inflows (Via TxIDs d0d98... and 4a761...) are sourced from an entity we will discuss in more detail later in this report.
The deposits into the Intermediary wallet are not picked up by our graph traversal heuristic which is bounded by separate wallet fingerprints, in this case Wasabi CoinJoins.
The delayed spike in inflows becomes apparent after the coins are partially mixed through Wasabi. This presents an added complexity to the simple volume and timing analysis we had performed for ChipMixer.
Linking Postmix Spends
So far, we have identified a preliminary list of likely ChipMixer outputs attributable to the original KuCoin theft based on volume and timing analysis. Having identified Blender, we further refined our search based on the following:
- Using our ChipMixer preliminary list as a basis, we searched for transactions combining outputs from both mixers.
- After developing a new preliminary list with spends from both mixers, we noted two additional patterns:
- A first transaction consumed P2PKH outputs from each mixer with an identical fingerprint (Version #2 and locktime = blockheight). This is the same fingerprint as the "Stolen Fund Wallet" responsible for making the mixer deposits.
- Outputs from these spends are used by a different wallet software with a new transaction fingerprint (Version #2 and locktime = 0). This wallet is responsible for initiating the long postmix spending peel chains.
These refined fingerprinting parameters had the effects of greatly reducing the number of likely false positives and allowed us to relax our original volume filter.
A summary of the results are provided in Table 3 below. Our "most likely" list of 54 transaction accounts for a little over 80% of the mixed BTC volumes. The complete list of our final transaction IDs is included in the resource spreadsheet (Tab 4).
| Deposit Stats | Withdrawal Stats | |||
|---|---|---|---|---|
| Dates | Volume (BTC) | Dates | Volume (BTC) | |
| ChipMixer | 26 to 28 October | 474 | 26 to 28 October | 460.74 |
| Blender | 30 October to 2 November | 534 | 30 October to 2 November | 381.96 |
| Subtotal | 26 October to 2 November | 1008 | 26 October to 2 November | 842.43 |
To summarize our rationale for this likely postmix spend transaction list.
- A volume and timing analysis based on ChipMixer inflows produced a preliminary list of outspending transactions of postmix UTXOs attributable to the KuCoin theft inflows.
- We then refined the list based on a wallet fingerprinting pattern of postmix spends from both mixers.
We have still not accounted for approximately 166 BTC.
The Intermediary Wallet
To review, the Intermediary Wallet received each of the non-ChipMixer deposits prior to spending exclusively to Wasabi CoinJoins. Up until this point we were unable to explain the role of the Intermediary Wallet.
Having developed a refined postmix spending list sourced from both mixers we can apply some additional timing analysis to further evaluate the function of this wallet.
| Event | Event Date | Event Block Height |
|---|---|---|
| ChipMixer Output Combined with Earliest Blender Outputs (TxID 1c1cb...) | 28 October | 654560 |
| First Premix Distribution to Intermediary Wallet (TxID 423d1...) | 30 October | 654741 |
| First Blender Tx With Outputs Combined with ChipMixer Outputs (TxID 520ca...) | 30 October | 654744 |
| First Spends of Intermediary Wallet to bech32 Outputs For Wasabi Partial Mixing (TxID f2c4e...) | 31 October | 654873 |
| First "Unmixed Change" Sweep from Wasabi to Blender Address (TxID 5b529...) | 1 November | 655032 |
The first Blender withdrawal that is spent with a ChipMixer output is made 3 blocks after the first deposit (in accordance with Blender's indicated workflow) to the Intermediary Wallet.
The first Blender outputs combined with Chipmixer outputs are created prior to the funds even being spent to bech32 addresses in preparation for Wasabi mixing.
The second takeaway highlights a possible paradox. How can the withdrawals from Blender be processed before the funds are sent to Blender?
These new observations suggest a strong interplay between the Intermediary Wallet and Blender and this interplay is likely the sign of a clever mechanism that may have two different explanations:
- Blender is the entity controlling the Intermediary Wallet, and they are responsible for sending funds to Wasabi.
In this scenario, Wasabi isn't really used as a proper mixer, but more like a tool used to split large UTXOs received by Blender. This usage has the benefit of an obfuscated splitting process that increases deniability for Blender. This scenario may be consistent with the identical footprint of the two wallets and with the observation of rather large "unmixed change" UTXOs leaving Wasabi. - A third party is in control of the Intermediary Wallet and this entity uses Wasabi and Blender sequentially for the obfuscation of funds.
In this scenario, the third party might be the provider of a "fast swap" service: as soon as funds are deposited to the Intermediary Wallet, some funds already mixed through Wasabi and Blender are released by the entity. The funds received by the Intermediary Wallet enter the mixing process later. Clients of this Entity get the benefits of mixing through the two services without the associated delay. This may also explain the premix transaction to [1DfKR...] (see Item B in Fig. 4) which possibly served as a kind of notification transaction alerting this entity to new incoming liquidity.
Postmix Spending Destinations
After developing a likely postmix TXID list attributable to the KuCoin theft, the next question becomes, where were the coins cashed out?
Typically in an attempted obfuscation scenario of this scale, the exchange destination becomes fairly obvious, but that has not been the case here.
The most common spending pattern of these postmix UTXOs appears to be following a very careful process. Long "obscure" peel chains of single UTXOs are frequently distributed in very small payments, typically less than 0.2 BTC to various destinations. Payment destinations from these peel chains appear random with end destinations including:
- One time use addresses
- Unlabeled Simple Spending Clusters
- Exchanges (Anything from Coinbase, Poloniex, Binance, to Bitzlato and more)
- Other services (ChipMixer, Wasabi CoinJoins, and Hydra Market)
- Occasional Volume Recycling back to Blender via Source "X", discussed below.
After the balance of each peel chain has dropped significantly, new UTXOs sourced from the mixers are combined with the previous peel chain and the process continues.
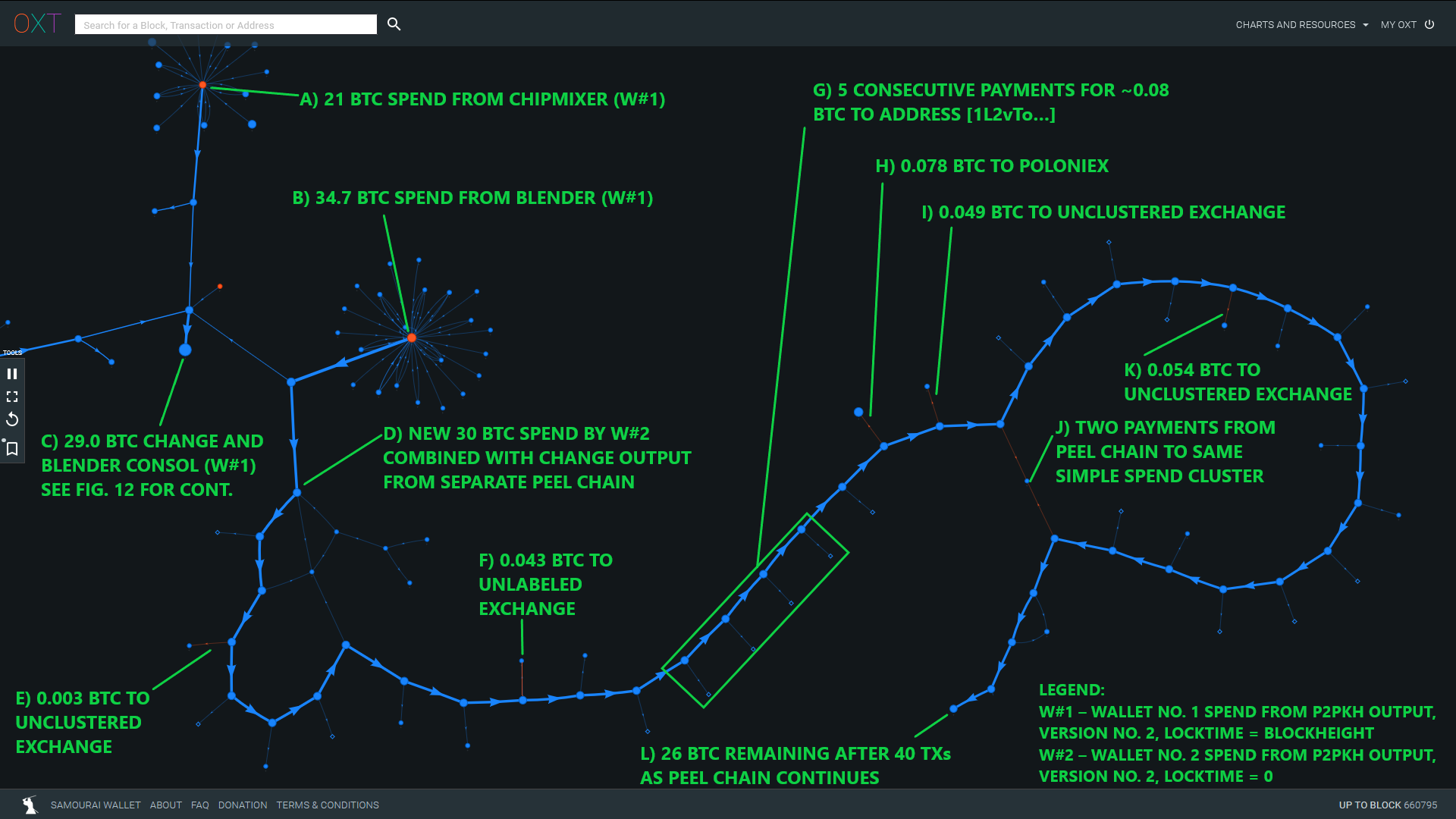
The labeled outputs from the peel chain are the only readily apparent spending patterns from this portion of the peel chain.
The non-annotated transactions are to single addresses or simple clusters that remain unspent since mid-November or have no readily apparent spending destination.
On one occasion, we noted ChipMixer and Blender outputs with very direct flows to several Binance and Bybit addresses. This portion of the transaction graph also includes large inflows from:
- Dozens of batch withdrawals sourced from unknown clusters or exchanges (ANON-3025909049 and ANON-3118782286). Each of these transactions merged exactly 21 inputs, each for approximately 1.5 BTC. Do these transactions represent a new obfuscation technique designed to fool risk-based compliance tools by diluting "high risk" coins with "low risk" coins?
- Hydra Market (+20 BTC withdrawals) sourced from long peel chains (TxIDs 233f1... and 57bd7...)
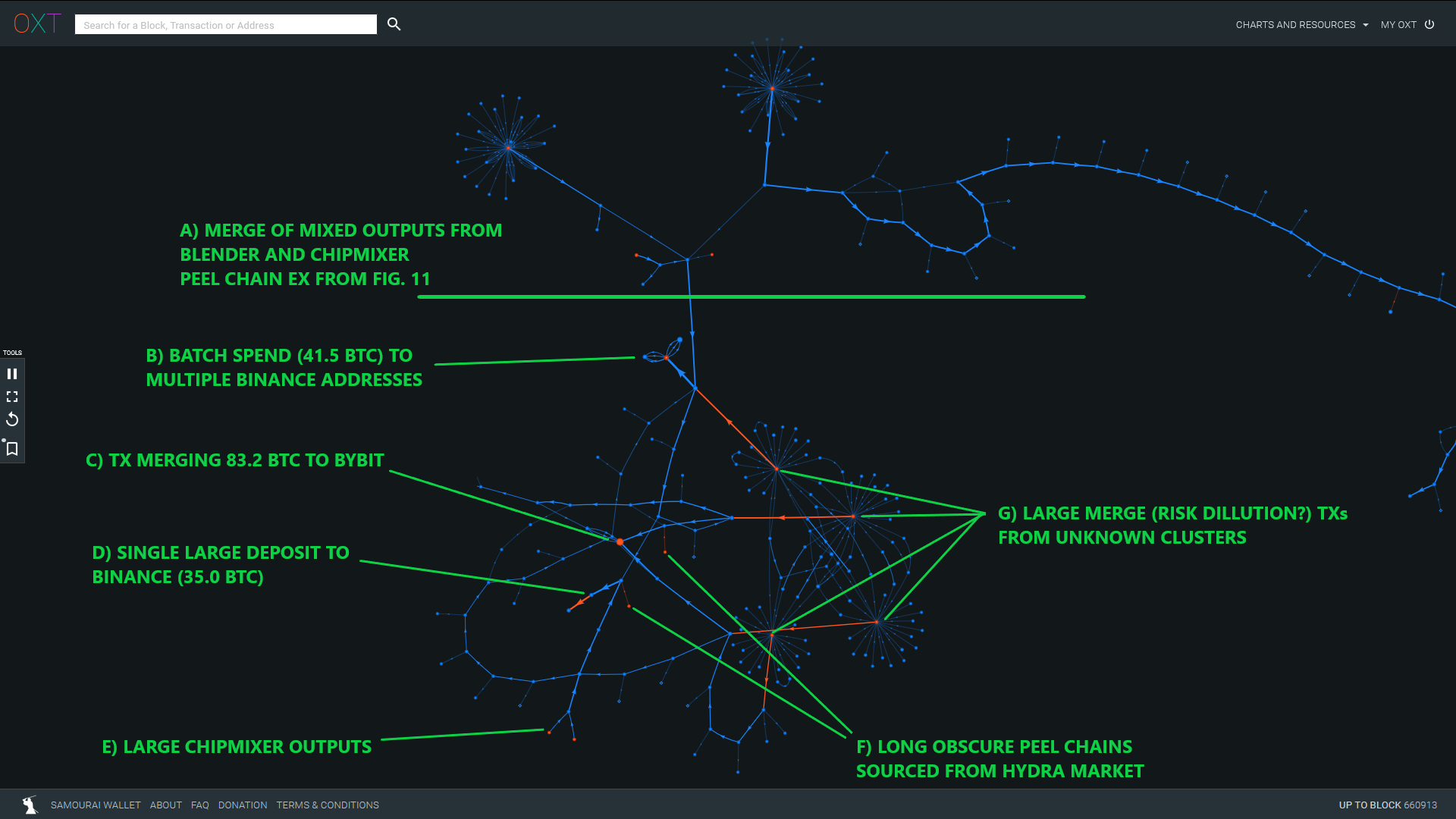
So far, the only consistent postmix pattern we noted was the wallet fingerprint switch between the first and second postmix spends. It's possible that this wallet switch represents the transfer of postmix UTXOs to a new entity (actual selling?), but this postmix spending patterns need further investigation.
A Birds Eye View
Generally, we have noted two distinct patterns centered around the discussed mixers during the relevant timeframe. This scheme is depicted below.
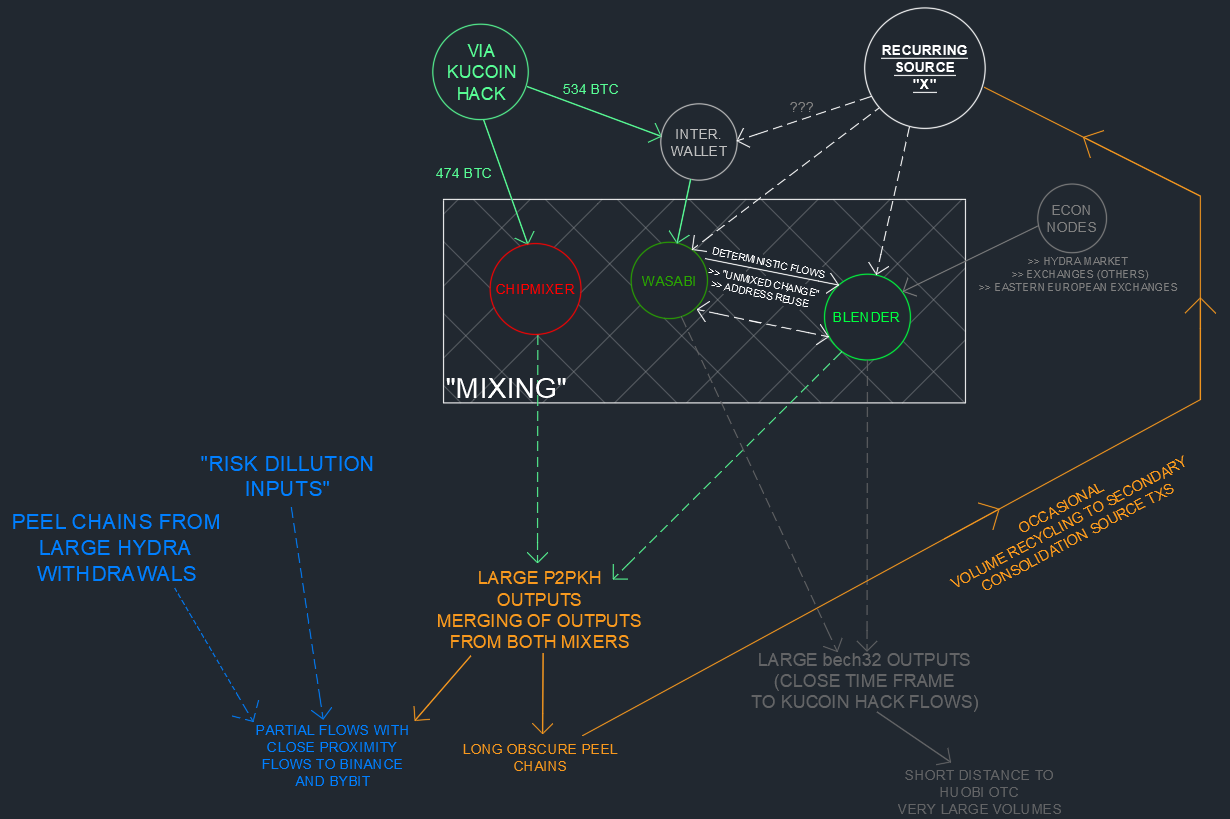
KuCoin Activity and Postmix Spending
The first noteworthy postmix spending pattern is characterized by the large P2PKH UTXOs sourced from ChipMixer and Blender meeting our noted wallet fingerprinting. These UTXOs are generally spent in long obscure peel chains as discussed above.
These peel chains pay to a variety of exchanges, otherwise unnoteworthy addresses/clusters, recycled Wasabi and ChipMixer volumes, Hydra Market, and occasionally recycle volume to Source "X".
Other Large Postmix Blender Activity
The other noteworthy (recurring) post-Blender spending patterns are made to large bech32 address formats. These are consolidated and sent to likely OTC activity centered around Huobi.
We have not attributed these flows to the KuCoin hack since the postmix spends from these addresses are processed prior to the KuCoin BTC entering Blender, but have included them here as a noteworthy and ongoing destination of large Blender volumes (see resource spreadsheet - Tab 5).
Source "X" (formerly known as the Hydra Whale)
We originally noted large recurring deposits to Blender/Wasabi in our "Lazarus Group Conspirator" report from March. At the time, we failed to identify Blender's involvement in the observed mixing process. This large recurring source of volume has been cycling coins through Blender and Wasabi CoinJoins for over a year (late October Inflows via TxIDs d0d98... and 4a761...).
This entity continues to operate at least two Wasabi mixing clients and suffer from address reuse/de-anonymization. In our "Lazarus Group Conspirator" report, we noted inflows of around 4500 BTC into this process between December 2019 and March 2020. Preliminarily evaluations of these Blender/Wasabi flows based on our newly identified Blender activity script put this estimate at closer to 20,000 BTC.
Unanswered Questions
Overall these observations raise more questions than answers.
- Are these large volumes Hydra market related?
- Is this a "white glove" laundering service making use of several mixers?
- Are we watching an abuse of Wasabi CoinJoins as an attempt to obscure Blender's reserve liquidity injections to "protect" Blender from identification?
Conclusions
The attempted obfuscation of the BTC stolen in the September KuCoin hack appears to be one of the most carefully formulated BTC obfuscation schemes. This process is second only to the recent spending patterns of the massive August 2016 Bitfinex hack.
While the flows identified in this report are not 100% certain, we believe our "most likely" transaction list serves as a good starting point for further investigation. To summarize our findings:
- Of the original 1008 BTC sourced from the KuCoin theft, 474 BTC were mixed via the custodial tumbler ChipMixer.
- The remaining 534 BTC were mixed using the custodial tumbler Blender in combination with apparent amount obfuscation by abuse of Wasabi coinjoins.
- We identified the recent behavior of both custodial tumblers including typical daily inflows and outflows.
- A volume and timing analysis was able to produce a preliminary postmix UTXO list sourced from ChipMixer.
- We then refined our postmix list based on close proximity spends from both tumblers and distinct wallet fingerprinting patterns.
- We have identified 842 of the 1008 mixed BTC.
- The exchange destinations of the stolen funds remain unclear at this time.
- The attempted obfuscation of the BTC sourced from the September hack has revealed a large and entity responsible for more than 20,000 BTC in Blender/Wasabi flows since December 2019.
Security researchers often spend a significant amount of time attempting to attribute specific malware to previously known hacking group activity. Researchers look for re-used code and formatting consistencies that can be used to draw parallels between otherwise separate events or malware.
The same theories can be applied to the blockchain activities of observed entities. In our case, the mixing and postmix activities encountered in our previous "Lazarus Group Conspirators" report are the closest analog to those observed during the KuCoin hack.

Our analysis leveraged the power of the OXT platform in combination with unique knowledge of bitcoin mixers and a flexible targeted evaluation to track the movement of these funds.
The OXT Research Team is intimately familiar with the analysis of special situations affecting bitcoin markets. With the help of the OXT platform, we remain uniquely situated to provide targeted transparent analysis of this and other special situations affecting bitcoin.
We will be continuing our reliable and verifiable investigations of these events. Any parties with questions relevant information that can aid in our ongoing investigation can contact us at investigations@oxtresearch.com.

