Understanding Bitcoin Privacy
This series provides you with a starting point for continuing to expand your understanding of bitcoin privacy. This series should be considered a prerequisite to understanding our other analysis and reports
Part I
In this section we introduce many of the basic concepts around bitcoin transaction privacy and learn several core heuristics that chain surveillance firms make use of.
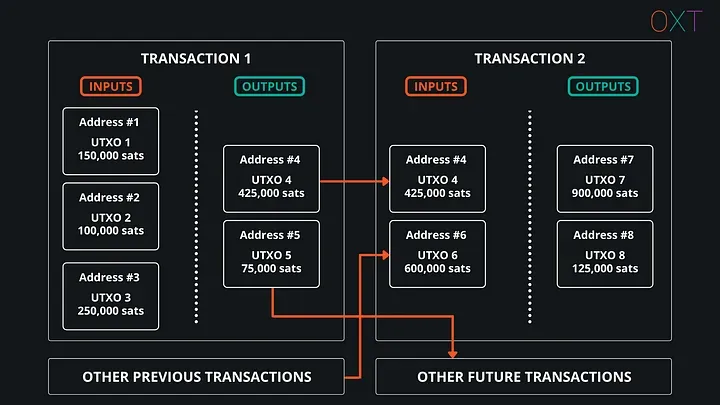
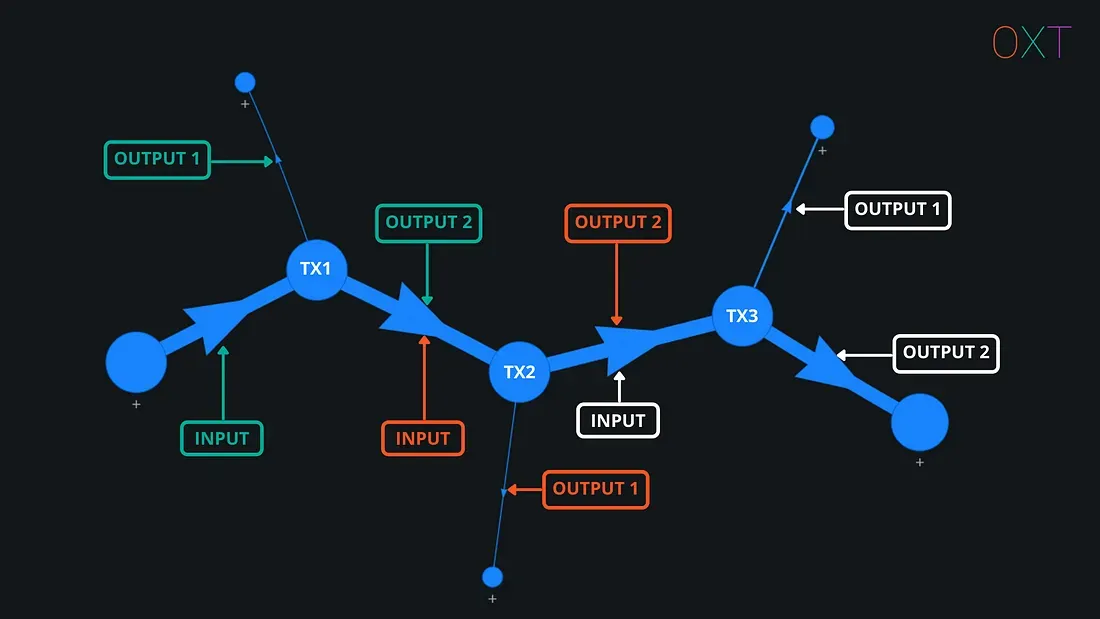
Part II
In this section we focus on two of the most important tools underpinning chain analysis: The transaction graph and the common input ownership heuristic (aka wallet clustering).
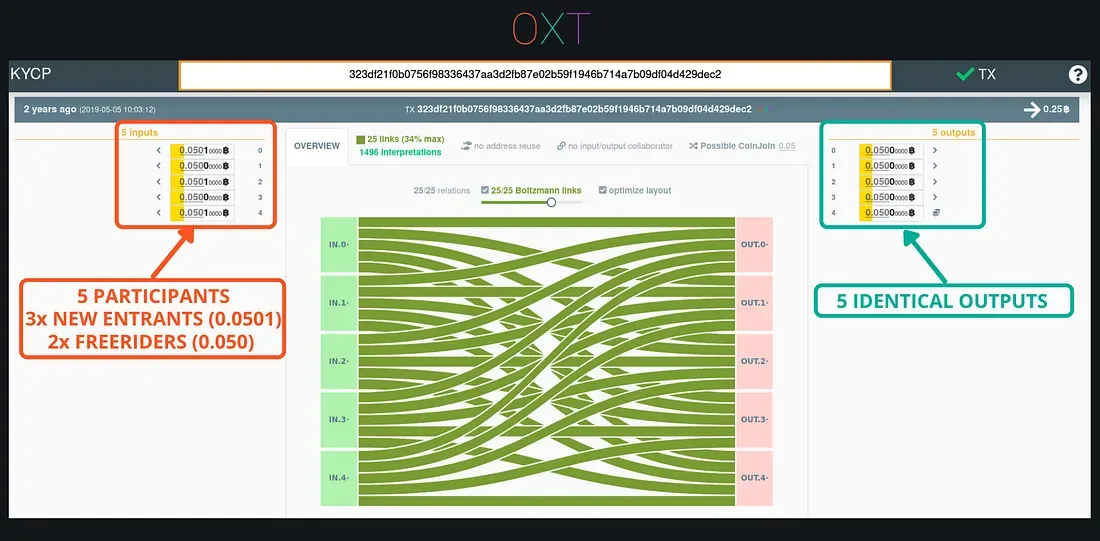
Part III
In this section we discuss methods for undermining chain analysis such as defeating heuristics, creating an ambiguous transaction graph, and using coinjoin.
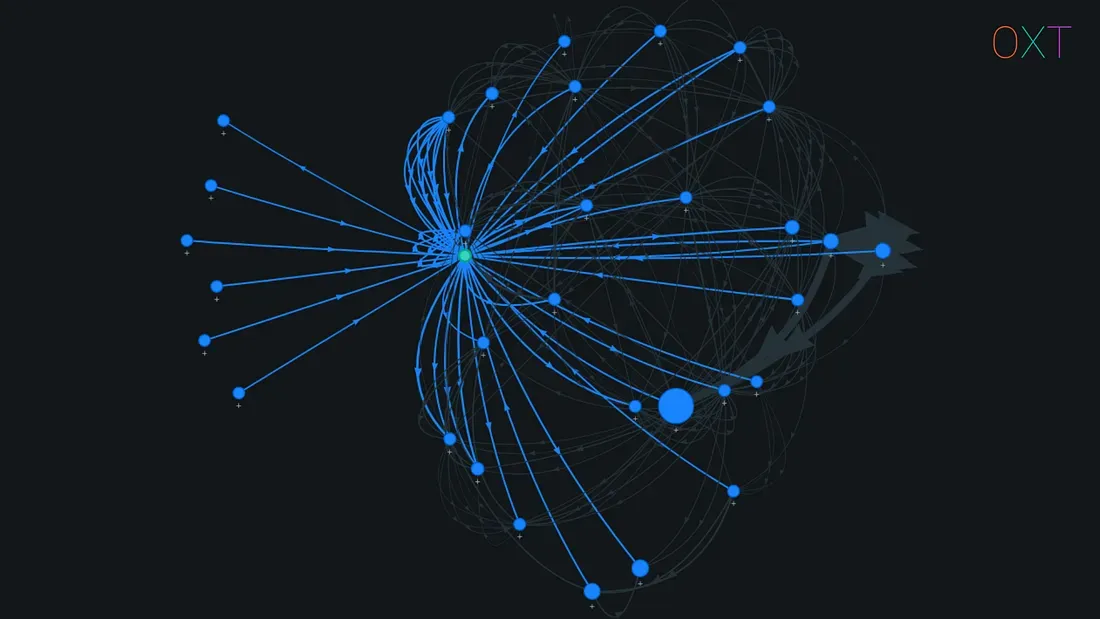
Part IV
In this section we review real world implications of sending and receiving transactions on user privacy and present specific privacy enhancing technologies that can be used to maintain privacy when interacting with bitcoin.